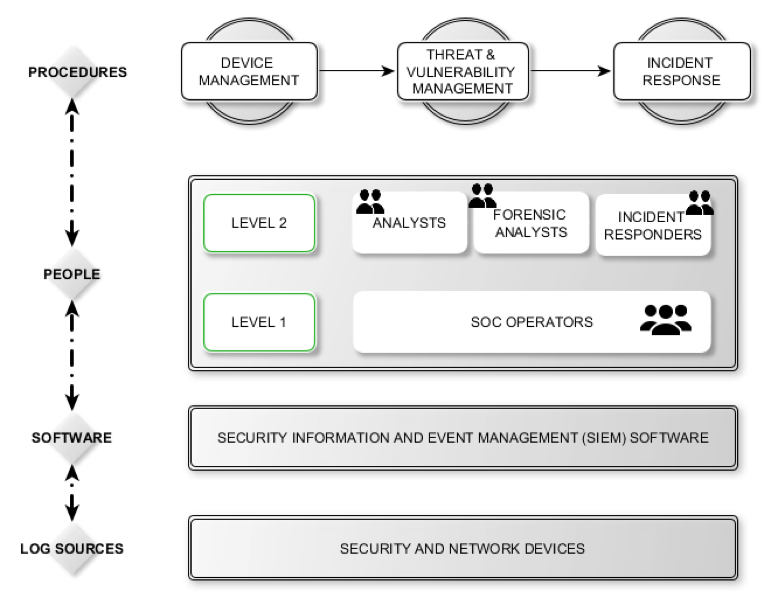
Security Information, Event Management & Security Operation Center
SIEM/SOC solutions are designed to provide real-time analysis of security alerts from within your organization’s network to maintain a secure environment while ensuring continuity of business operations.
It combines a set of tools, processes and cybersecurity experts to monitor networks and endpoints for vulnerabilities in order to protect sensitive data and comply with industry or government regulations.
Log Sources:
The log sources are the data sources from the network (routers, switches, firewalls, servers, endpoints, databases, applications, websites, and other systems) which rely on the SIEM to monitor and analyze activity on the network in real time.
SIEM Software:
The SIEM software collects and analyses data from a number of connected sources within the network via data flows, telemetry, packet capture, syslog, and other methods so that data activity can be correlated and analysed by the SOC team for anomalous activity that could be indicative of a security incident or compromise. The SIEM software also enables security teams to detect and respond to internal and external threats, reducing response time from hours or days to minutes.
People:
The security team comprises of members with a diverse set of skills and responsibilities, who monitor and analyse an organization’s security posture on an ongoing basis. The SOC team’s goal is to detect, analyse, and respond to cybersecurity incidents using a combination of technology solutions and a strong set of processes.
Procedures:
The set of procedures are needed to ensure that all incidents are correctly identified, analysed, defended against, investigated, reported, and responded to appropriately.
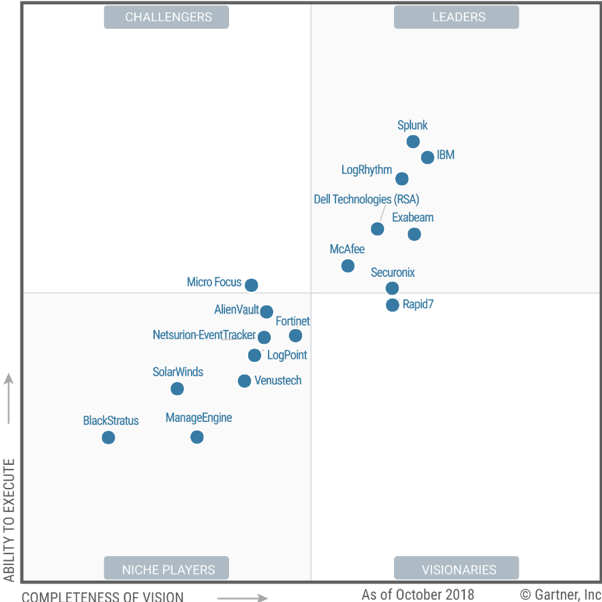
CyberHawk specialises in implementing complete SIEM/SOC solutions covering the needed tools, processes, human resources (operators, analysts, SOC manager, forensic experts, incident responders and research & intelligence experts) and using SIEM software from Gartner’s Magic Quadrant.