Fake, positive reviews have infiltrated nearly every corner of life online these days, confusing consumers while offering an unwelcome advantage to fraudsters and sub-par products everywhere. Happily, identifying and tracking these fake reviewer accounts is often the easiest way to spot scams. Here’s the story of how bogus reviews on a counterfeit Microsoft Authenticator browser extension exposed dozens of other extensions that siphoned personal and financial data.
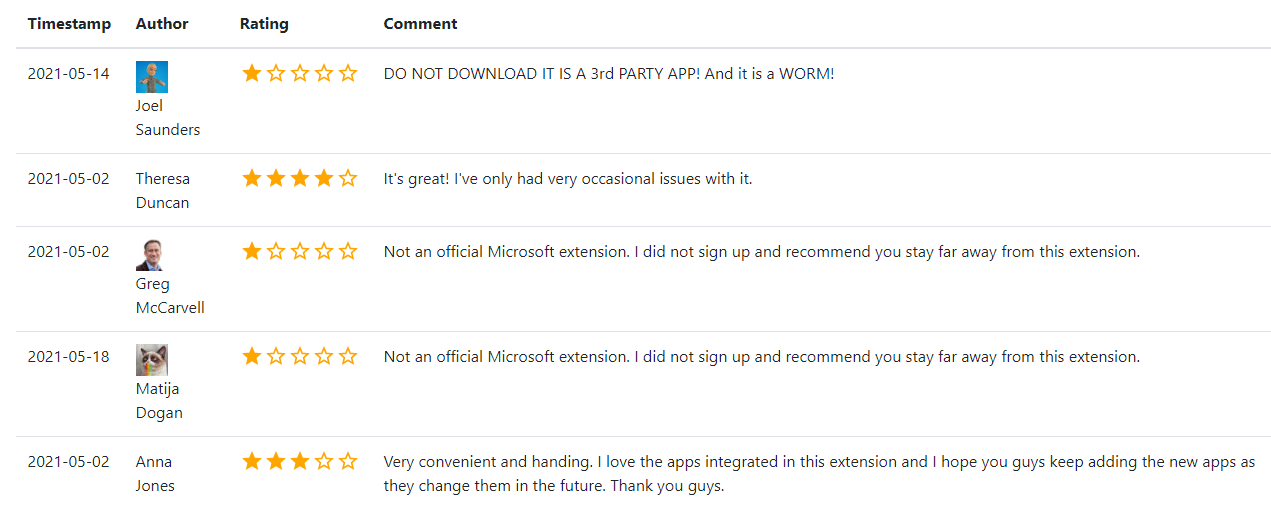
Comments on the fake Microsoft Authenticator browser extension show the reviews for these applications are either positive or very negative — basically calling it out as a scam. Image: chrome-stats.com.
After hearing from a reader about a phony Microsoft Authenticator extension that appeared on the Google Chrome Store, KrebsOnSecurity began looking at the profile of the account that created it. There were a total of five reviews on the extension before it was removed: Three Google users gave it one star, warning people to stay far away from it; but two of the reviewers awarded it between three and four stars.
“It’s great!,” the Google account Theresa Duncan enthused, improbably. “I’ve only had very occasional issues with it.”
“Very convenient and handing,” assessed Anna Jones, incomprehensibly.
Google’s Chrome Store said the email address tied to the account that published the knockoff Microsoft extension also was responsible for one called “iArtbook Digital Painting.” Before it was removed from the Chrome Store, iArtbook had garnered just 22 users and three reviews. As with the knockoff Microsoft extension, all three reviews were positive, and all were authored by accounts with first and last names, like Megan Vance, Olivia Knox, and Alison Graham.
Google’s Chrome Store doesn’t make it easy to search by reviewer. For that I turned to Hao Nguyen, the developer behind chrome-stats.com, which indexes and makes searchable a broad array of attributes about extensions available from Google.
Looking at the Google accounts that left positive reviews on both the now-defunct Microsoft Authenticator and iArtbook extensions, KrebsOnSecurity noticed that each left positive reviews on a handful of other extensions that have since been removed.
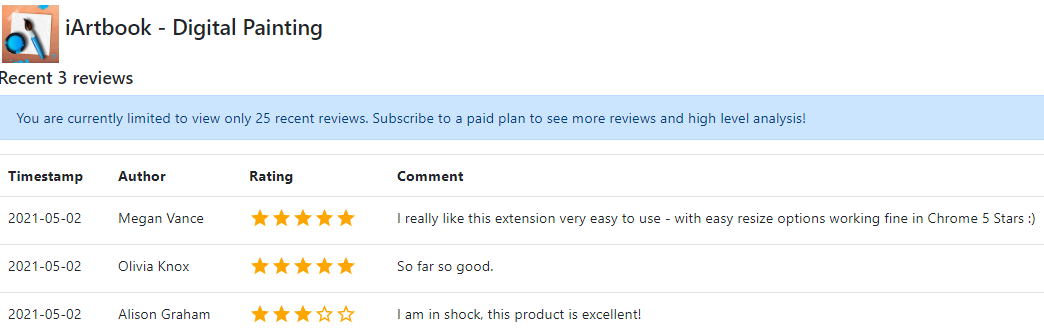
Reviews on the iArtbook extension were all from apparently fake Google accounts that each reviewed two other extensions, one of which was published by the same developer. This same pattern was observed across 45 now-defunct extensions.
Like an ever-expanding venn diagram, a review of the extensions commented on by each new fake reviewer found led to the discovery of even more phony reviewers and extensions. In total, roughly 24 hours worth of digging through chrome-stats.com unearthed more than 100 positive reviews on a network of patently fraudulent extensions.
Those reviews in turn lead to the relatively straightforward identification of:
-39 reviewers who were happy with extensions that spoofed major brands and requested financial data
-45 malicious extensions that collectively had close to 100,000 downloads
-25 developer accounts tied to multiple banned applications
The extensions spoofed a range of consumer brands, including Adobe, Amazon, Facebook, HBO, Microsoft, Roku and Verizon. Scouring the manifests for each of these other extensions in turn revealed that many of the same developers were tied to multiple apps being promoted by the same phony Google accounts.
Some of the fake extensions have only a handful of downloads, but most have hundreds or thousands. A fake Microsoft Teams extension attracted 16,200 downloads in the roughly two months it was available from the Google store. A counterfeit version of CapCut, a professional video editing software suite, claimed nearly 24,000 downloads over a similar time period.
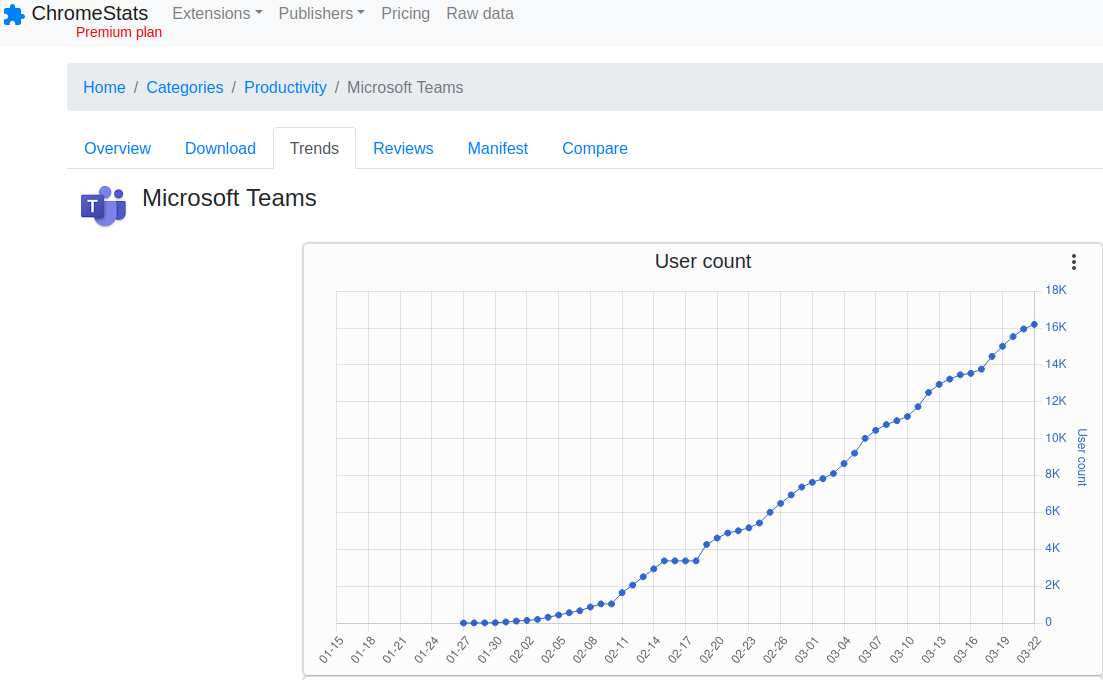
More than 16,000 people downloaded a fake Microsoft Teams browser extension over the roughly two months it was available for download from the Google Chrome store.
Unlike malicious browser extensions that can turn your PC into a botnet or harvest your cookies, none of the extensions examined here request any special permissions from users. Once installed, however, they invariably prompt the user to provide personal and financial data — all the while pretending to be associated with major brand names.
In some cases, the fake reviewers and phony extension developers used in this scheme share names, such as the case with “brook ice,” the Google account that positively reviewed the malicious Adobe and Microsoft Teams extensions. The email address brookice100@gmail.com was used to register the developer account responsible for producing two of the phony extensions examined in this review (PhotoMath and Dollify).
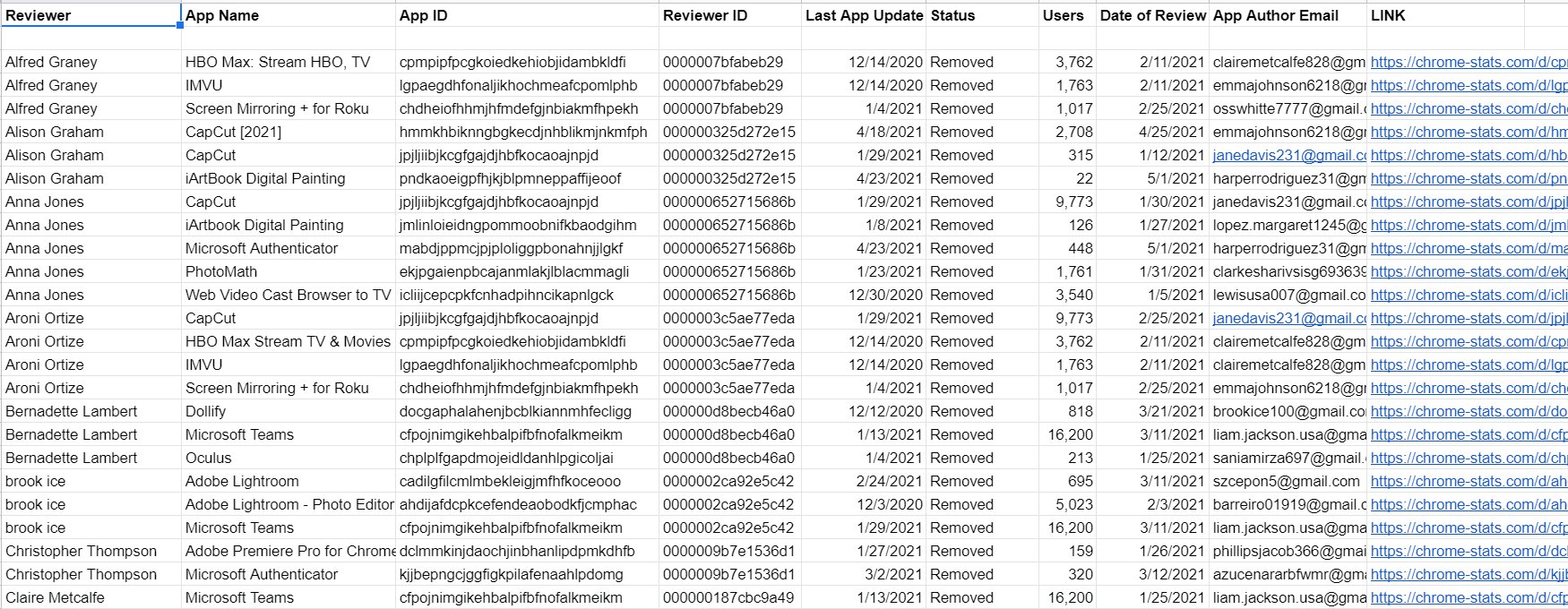
Some of the data that informed this report. The full spreadsheet is available as a link at the end of the story.
As we can see from the spreadsheet snippet above, many of the Google accounts that penned positive reviews on patently bogus extensions left comments on multiple apps on the same day.
Additionally, Google’s account recovery tools indicate many different developer email addresses tied to extensions reviewed here share the same recovery email — suggesting a relatively few number of anonymous users are controlling the entire scheme. When the spreadsheet data shown above is sorted by email address of the extension developer, the grouping of the reviews by date becomes even clearer.
KrebsOnSecurity shared these findings with Google and will update this story in the event they respond. Either way, Google somehow already detected all of these extensions as fraudulent and removed them from its store.
However, there may be a future post here about how long that bad extension identification and removal process has taken over time. Overall, most of these extensions were available for two to three months before being taken down.
As for the “so what?” here? I performed this research mainly because I could, and I thought it was interesting enough to share. Also, I got fascinated with the idea that finding fake applications might be as simple as identifying and following the likely fake reviewers. I’m positive there is more to this network of fraudulent extensions than is documented here.
As this story illustrates, it pays to be judicious about installing extensions. Leaving aside these extensions which are outright fraudulent, so many legitimate extensions get abandoned or sold each year to shady marketers that it’s wise to only trust extensions that are actively maintained (and perhaps have a critical mass of users that would make noise if anything untoward happened with the software).
According to chrome-stats.com, the majority of extensions — more than 100,000 of them — are effectively abandoned by their authors, or haven’t been updated in more than two years. In other words, there a great many developers who are likely to be open to someone else buying up their creation along with their user base.
The information that informed this report is searchable in this Google spreadsheet.
I use Fakespot Chrome plug-in to spot fake reviews on Aamzon.com and eBay. It says it used “artificial intelligence that has been trained to pick up on patterns.” It scans for reviewers and then checks there other reviews. Sounds like a similar AI/ML approach could be tried with these app stores with other attributes added like how often the apps is updated.
I am sure I’m missing out on a lot of opportunities by not using plug-ins. Having said that, my first reaction was “so, how do I know that “Fakespot” is legit / stays legit? (see Phil’s comments later in the comment list) My second thought was “if Fakespot is good at what it does, then why doesn’t Amazon automatically run something like that and remove (or annotate somehow) more suspicious comments for everyone and not just Fakespot users. Clearly, I’m wading through a lot of my own ignorance here – but thank you for your comment – it gives me more to think about.
Good questions.
1. How do we know Fakespot is legit: While you can never be 100% certain I did look into the company and the people who founded it and came away satisficed that they are legit.
2. Stays legit? We can’t be sure unless we constantly check back and see if anything has changed.
3. “if Fakespot is good at what it does, then why doesn’t Amazon automatically run something like that and remove (or annotate somehow) more suspicious comments for everyone and not just Fakespot users.”
Because your assumption that Amazon cares about it’s customers is clearly wrong. They care about profits and as long as they can claim that are trying, most people happily buy products on Amazon.
Simplest: Don’t use Amazon.
Amazon doesn’t want to stop fake reviews because they profit on fees from sales, even for crap products. It’s an inherent conflict of interest, but they’ll bust the most egregious offenders and make a show out of it to look like they’re doing something occasionally.
One question – Did you even look at the permissions for Fakespot??
I did, and you must agree to hand over the keys to the kingdom.
Not me.
Very eye-opening article. As a rule of thumb, it might be wise to only use extensions that have existed for a longer period of time. Never hop onto a new extension when it first appears. Good to see that Google is apparently actively looking for such fraudulent extensions. I learn a lot by reading Krebs on Security.
> Never hop onto a new extension
Then who will ever try it ?
> Then who will ever try it ?
Possibly security researchers with sandboxed browsers running on firewalled machines under operating system devoted to development/forensics and not containing any personal data.
I don’t agree with you. If you remember what has happed with The Great Suspender extension which was used by millions of people.
So, users are at risk whether the extension is new or old. It all depends on the developer’s intent.
I knew a “Christian David” and the stories he had about companies refusing to believe that his name was actually that, or the comical glitches that occurred (likely due to a person trying to “fix” it) were wonderful. I also knew someone with the surname James because INS mixed up his dads first and last name and fixing it would be a Herculean task (“computer says no”). So please be careful using “firstname firstname” as an indicator of shenanigans, a lot of legitimate people will get nailed.
Hi Kurt. You are mistaking statisical analysis for logical inference and assuming that the author is doing so as well. Ignoring statistical anomalies is extremely unwise when examining known illicit activities. Perhaps its best to let the professionals make determinations of relavence with the understanding that it -to be direct, blunt, or frank about it- might not be their first rodeo.
Just a thought and yes, eveyone eight years and older here knows the dangers of using a single taggant to infer anything. We all understand your need to remind us is likely do to you being threatened by the revelations being made but those of us not threatened and indeed curious moreso than anything else would also appreciate you not projecting your insecurities onto the rest of us.
There is a lot of shady stuff going on and Krebs reports on the tiniest fraction of a percent of it. The pros have got to get better at physical analysis, having become over reliant on ML to police giant user bases they have created. Governments have the same problem and the difference between a government governing/policing its user base and tech companies is astonishing.
Tech companies are oblivious to the vast scope of the new problems their tech can create, which is why they police them as little as they do and are often found falling short again and again.
If you work in IT and that’s the real reason you are cautious of using statistical analysis as a means of punching back at being held to account for a percieved past failing, then take it on the chin, stop obfuscating and move on. Do better, get better.
The TLDR version of that is LEARN STATISTICS AND LOGICAL FUNDAMENTAL ANALYSIS, then do whatever!
You’ll be better at it, 5 sigma sez. Go team.
Huh?
BTW, there’s no such thing as a statistical anomaly. It’s a dumb term used by those who can’t explain particular data points and usually hear “Try again” when they use it. Copious derision precedes that advice.
I think it might be more useful if the apps could adopt an independent certification that their source code was found to be clean, that they have not been sold off to bypass security checks and that they do not cause issues whether intentional or not. Google is unable to moderate their own store, so maybe there needs to be another website with a short list of safe apps?
This reminds me a lot of how I would track and clear out scam email accounts on a email provider I worked at twenty years ago. I’d start with the IP address of the account that had been confirmed to be spamming scam emails (inevitably Nigerian-style) and see what other email addresses came up from that IP. Then run a grep through those accounts for key phrases used in Nigerian scams and confirm those instances. Check the IPs on those, and you’d end up with an entire tree of scam accounts shut down from a single report.
Best of all, you could do this without violating anyone’s privacy by just looking for the obvious key word combinations.
Thanks for sharing the information !
I sorted the spreadsheet by email address…. it’s nice of so many people to share the same address, eh?
Thanks Brian, another super interesting post.
Do we have these resources for Apple and Firefox?
make it a habit of NOT providing real personal info when getting online. use fake names, addresses, etc.,
My credit card company and bank will be thrilled if I try that.
What I don’t get is : why are people so eager to use their phones with app that use WiFi from God-Knows-Where?
I have none of that stuff on my phone and I don’t even have email activated… why make it the easy for the crooks to get your stuff? Is checking your balance so important that you would risk ID theft ?????
Having done a ton of work with decryption, I can tell you that trusted phone apps are WAY more secure than the web versions (your bank, gmail, etc…). Almost all phone apps have pinned certs. Even if you are malicious wifi, the pinned cert app can’t be man-in-the-middled. Hopefully it will warn the certs don’t match and won’t connect. At worse, it simply won’t work.
Your browser on the other hand, there are lots of ways to break that without an average user noticing much.
If you could do this in just 24 hours, imagine what Google could do – automatically or manually – with the database right there in front of them. One might say that they had a duty to do so, but I don’t see that becoming a legal reality anytime soon.
It’s almost as if Google is a Spy organization first, and nothing second.
It’s a Marketing powerhouse. So you are not too far off.
People who post reviews want them to be read. I can’t ever figure out why users can’t search by reviewers. Would help a lot to tell real from fake ones! But, of course, we users are not Google’s customers. We are merely one of their numerous products. Why empower us???
It’s almost as if Google is a Spy organization first, and nothing second.
Keep going with that train of thought.
If you get goog to answer questions, might ask them; Why they don’t send notices out to people that have downloaded an app (email required to DL) that was removed for malicious purposes.
Google and other major providers have built this lack of integrity into their business models. Rewards exist for increased volume (in the tally of developers, apps, or downloads) but not for protecting users. The providers could reduce and largely eliminate such threats via methods less complex than those they invoke to convert traffic into money. As you demonstrated, it took only a few days and a spreadsheet to document a tremendous vulnerability. A similarly gross example may be familiar to any Facebook group admin. Watch for a request to join from a recently created account, with a visibly peculiar name (as in your example). Click to their profile. It’s common to see a new FB account, with one professional photo, and 75 new friends in the past 24 hours, each with a name of the same degree of peculiarity. Click to any of their friends. They’ll also have one professional photo, with 75 new friends in the past 24 hours. Once you’ve documented the first ten, submit them to Facebook for review. FB will respond that this does not conflict with their Terms of Service. FB ~knows~ that these are fraudulent account, but FB ~values~ those accounts more highly than the integrity of the platform.
I tend to look at reviewer names, if they’re generic and use awful grammar, over the top phrasing, bizarre spelling and key/trigger words, they’re fake or at least useless. Amazon runs clicknets, search for something like “the one it but what” and Amazon has a link! The google stuff is no surprise at all, the company whose browser they call “browser based used ad data collection software” or something like that.
It’s confusing, there’s a Chinese company called Generic that sells some good stuff but their name? Created by Google Translate maybe? My approach to anything online is it’s fake until it isn’t.
This stuff won’t end until it’s legislated and enforced, a herculean task. Users won’t change anything. Minor waves of users smarting up wax and wane but there are so, so many gullible people online, racketeering will continue to live large. Cults of The Impossible and Improbable are everywhere and growing; they aren’t parodies, the Froot Loops in them have finally found a community that “Will just listen to me!”
Is the market for Stupid bottomless? IDK but it sure seems to be regenerative.
“Why Is Your Location Data No Longer Private?”
short answer:
Because under common law your location has never been private. https://twitter.com/Olympic2021Live
Remember when Apple and Google promised increased security by only installing apps from their app stores? Then they locked down phones, tablets, and even computers from installing 3rd party software on ostensibly security grounds. And charged for it. Me: I’d rather choose my own software. The tech monopolies are doing a terrible job of it.
“Me: I’d rather choose my own software.” – Oh no doubt, what’s your RE/fuzzing setup?
Grandma: “I’ll click anything with solitaire or bingo in the name.”
Salesderp: “Clicked popup, now updating flashzooms but takes forever closing ads.”
Adolescent: “PokemGoof.app wants to access your library, camera, mic, contacts, email”
They provide an observable improvement to the default state of zero effort users.
Perfect, nope, flawed even conceptually no doubt, but an improvement.
Too bad, when you develop popular software, make billions and corner the market, then you can dictate what you see in the app store.
Remove the star rating from the initial app entry in the store. Just have “Reviews”. This invites the user to proactively initiate their investigation. Once clicked/tapped you are then presented with something like:
This app has 21 Reviews:
Negative (1-2 stars) 11
Average (3 stars) 6
Positive (4-5 stars) 4
Users can then immediately see that there are negative reviews present and I would think that people might be more likely to read more about the negatives. App stores should also prevent apps with disproportionately more negative reviews showing at the top of search results.
Something’s wrong here — I am getting a stale, week-old cached view of this site’s front page. None of this week’s new posts are visible to me, though I can see comments that are younger than that. This article here still shows as the most recent for me, though there should be between three and five newer ones.
Something’s wrong here — I am getting a stale, week-old cached view of this site’s front page. None of this week’s new posts are visible to me, though I can see comments that are younger than that. This article here still shows as the most recent for me, though there should be between three and five newer ones.
And it eats new comments instead of posting them. Lovely.
Is there any reason to think extensions for Firefox are more secure? Or, given Firefox’s declining share of users, should we be *more* worried about security issues (because Firefox has less staff to monitor). ?
I don’t think staff level matters. Neither want to do a manual review process.