If you hand your credit or debit card to a merchant who is using a wireless point-of-sale (POS) device, you may want to later verify that the charge actually went through. A top vendor of POS skimmers ships devices that will print out “transaction approved” receipts, even though the machine is offline and is merely recording the customer’s card data and PIN for future fraudulent use.
This skimmer seller is a major vendor on one of the Underweb’s most active fraud forums. Being a “verified” vendor on this fraud forum — which comes with the stamp of approval from the forum administrators, thus, enhancing the seller’s reputation — costs $5,000 annually. But this seller can make back his investment with just two sales, and judging from the volume of communications he receives from forum members, business is brisk.
This miscreant sells two classes of pre-hacked wireless Verifone POS devices: The Verifone vx670, which he sells for $2,900 plus shipping, and a Verifone vx510, which can be had for $2,500. Below is a video he posted to youtube.com showing a hacked version of the vx510 printing out a fake transaction approval receipt.
From the seller’s pitch: “POS is ‘fake’ and stores D+P [card data and PIN], prints out approved receipt or can be setup for connection error. Software to decrypt the data is provided. It keeps d+p inside memory for manual retrieval via USB cable.”
These types of hacked POS systems, known as “offline POS skimmers” in the Underweb, are marketed for suggested use by miscreants employed in seasonal or temporary work, such as in restaurants, bars or retail establishments.
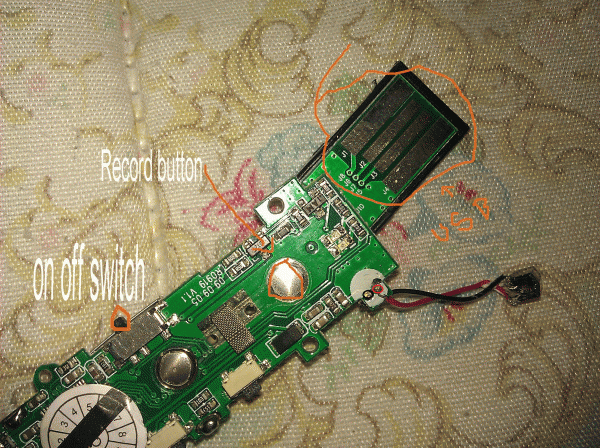
The fraudster selling these skimming devices also sells regular ATM skimmers, including a skimmer model that was featured in an earlier post on KrebsOnSecurity. That device, made to fit over the card slot on certain models of Diebold Opteva ATMs, records the data stored on the magnetic stripe of a card using a disassembled MP3 player. Below is a close up that the skimmer seller provides to customers, showing the MP3 player circuit board used in his skimmers. This is part of a card skimmer that is sold with a hidden camera that is built into a false panel made to be affixed directly above the cash machine’s PIN pad.
The stolen card data from this Opteva skimmer is stored as an MP3 file, and can only be decoded with special software. To hear what those audio files sound like, check out this sample, which the skimmer seller supplies to customers who ask for instructions on decoding the MP3 files.
Below are a few more images of the card skimmer as shipped to buyers.


Another interesting and sobering article again.
I was just thinking the other day how much more secure “pay-by-bonk” (PayPass and similar payment systems where the customer simply taps the card against the POS terminal to pay) is compared to inserting your card and entering the PIN. Or at least it is provided the card or device is in your possession.
I suppose this will come under attack soon enough though.
you mean NFC / RFID? you might want to check this video
http://youtu.be/GjOduug-SC8
I wonder how long before they crack Chip-‘n-pin; if they haven’t already?
I suppose this will come under attack soon enough though.
HA-HA-HA-HA .
Yes it will come under attack from now on .))) What a weird way of thinking . its been going on for Years and years its just Brian and his team of helpers just got to it now . Must be run out of any dissent story’s to print .
By “secure” do you mean inherently more secure or just that NFC exploits aren’t common yet?
This attack will be just as effective against NFC payments.
Unnecessary of course, as NFC allows unvalidated payments up to a fixed amount without any interaction at all. After 10 seconds with a friend’s RFID scanner, I’ve replaced my wallet with one containing a wire mesh.
Would it be a viable defense for customers to first enter a wrong PIN as a matter of habit?
Or would the POS be active enough to check the correctness of the PIN with the card anyway?
Without being any sort of expert I expect not since the crook can just use the last 4 digits. Although having said this I have no idea if 4 digit pins are standard across the world – they seem to be in AU.
Perhaps it would pose more difficulty if pins varied wildly in length but it wouldn’t make it impossible to find the correct length. And if the keystrokes are timestamped forget about it, the thief has your account.
It was thinking that the POS did not verify the PIN at all, and just accepted any PIN provided, it being offline. But I guess the POS can verify the PIN offline with the card itself (have yet to see a compelling argument for that misfeature…)
To be PCI compliant at POS can’t store card or PIN data. If the POS is in offline you should not get an authorization. I’ve provided two links to help you get learn more about PCI. By knowing the standards merchants are to be at can help you prevent fraud on your card.
https://www.pcisecuritystandards.org/
http://www.pcicomplianceguide.org/pcifaqs.php#23
People manufacturing skimmers are not trying to be PCI compliant.
it likely checks the pin first. i mean, im from the UK and our banks can provide a card reader for when you make online purchases so you can use your card and you have to verify the pin. so machines out there can easily check the pin is correct or not when they type it so i would assume this feature exists for the later model here. if not it should be
this story must be at list 4 years old .Old news again Brian .
This place become more like a Russian criminal underground NEWS report blog .
it only goes up to someone steal something or wants to steal or trying to steal something .Nothnig else
u need to get a job at the POLICE Brian you are well go at it ..
Interesting. This post mentioned nothing about Russians.
Brian i didn’t said in this post , i said this blog — become more like a Russian criminal underground NEWS report blog . Journalists always assume/imagine/invent things in the heads .
80 % of your blog is about Russians or it have something to do with Russians .
such a shame that This post didnt mentioned nothing about Russians.Shame on you Brian .
But u must agree that this so called NEWS are at list 4 years old .
If you don’t like him talking about your part of the world, you should do something about the scam artists living in your midst.
If I don’t want to be associated with criminals and scumbags, I don’t hang out with criminals and scumbags.
A few comments: “so What” why are you even reading this blog if you have such disdain for the content? Secondly, your diction is so terrible you should think twice before commenting. Thirdly, maybe it’s because there is an inordinately high number of crooks in Russian that these stories tend to talk about Russian crooks. And finally – the news in this post relates to off-line skimming with fake receipts, and the related You-Tube marketing effort. The stories you linked to are not about off-line skimming. The news in this case is more about this particular thief, not that skimming is new.
Point about Chip/PIN technology: the PIN is embedded in the chip and requires to be duplicated by the card owner in the device, before a transaction commences.
Kevin,
I think “diction” means when you’re actually speaking, it’s “So Whats’ ” grammar that is awful. But you’re absolutely 100% right.
Peter
Wouldn’t the merchant/employer have an issue with this if an employee used this but did not run the real transaction as well?
I would guess that the miscreant would switch his employers terminal for one of these, then in a week or two swap them back. That way the problem is distributed across all staff, instead of just being tied to a particular individual.
Unfortunately, they’ve used with success (for the thieves), here in WestEurope, an even less sophisticated scam: They ring at elderly people (80+) and tell them they received a parcel / present but they have to pay (by pin) a small fee (tax, transportation, whatever) of a few Euro. Then they produce a (fake) mobile pin machine like above and let the victim attempt to pay. The machine gives some transaction errors, even after the miscreate “helpfully” oblige to assist the victim to introduce the pin correctly. then they go (without leaving the fake parcel) and claiming they will come back later, when the company will fix the pin machine outage. Later the victim observes the card was actually switched with somebody else’s card (remember the victims are picked to be elderly). Meantime the thief with the real card and the pin he eavesdroped earlier empty the bank account. The cycle is complete when he uses the now empty card to switch with the card of his next victim. So it doesn’t even have to record pin or magnetic track, if it has a display, a keyboard and some leds and the victim is handpicked to be elderly, those disgusting rats can pull it off even in the area where EMV has replaced the magnetic stripe.
Hi George,
This type of scam is becoming more of a problem as the Daily mail has been reporting, over the last week or two. Sadly it is easy money for the scum bags.
http://www.dailymail.co.uk/money/saving/article-2244134/Rise-telephone-scam-targeting-older-British-credit-debit-cardholders.html
http://www.dailymail.co.uk/news/article-2249752/A-999-credit-card-scam-cost-thousands.html
Thanks again, Brian for your research into this and other security-related topics. I see this, and various other articles by you, cited in other publications, including OSAC.
Hi.
This is now happenning in Chile last month. There have been about 5 cases in gas stations. The fraudulent visit gas stations and deceive staff personnel posing as the supplier of POS in order to change it for a fake one.
Police show comparatives between real and fake vouchers, but this will be a temporary solution when fraudsters improve their technique :
http://www.emol.com/noticias/nacional/2012/12/16/574873/maquinas-de-cobro-falsas-detectan-nexos-de-lider-de-banda-con-chileno-preso-en-argentina.html
Here is news when the band was arrested:
http://www.emol.com/noticias/nacional/2012/12/11/574000/cae-banda-que-clonaba-tarjetas-con-maquinas-cobro-inalambrico-falsas.html
here is the same old story from 2007 ..u need to get a grip Brian .your story’s sucks .
http://www.highbeam.com/doc/1G1-172522216.html
here is one from 2010
http://www.theregister.co.uk/2010/03/15/fradulent_payment_card_processors/
who are u kidding ????
I can’t really say I am suyprised by this at all. This is a way better option that sticking something over an ATM and catching the info that way if you think about it. There was a case similar to this in the city I live in where the cashier at a national chain gas bar was helping the crooks skim the information from a pos terminal that had been tampered with. He would change it out with the proper terminal once his shift started, and then put the original one back in once the shift ended. The company got wise about 6 months later when they realized there nightly sales were dropping at an exceptional rate over a 6 month period, so they started checking and installed a hidden camera thinking the employee was skimming cash. Well the hidden camera caught the employee switching the pos terminal.. and then they delved into it and knew they had a huge issue and contacted the police. Once it became known in the media that charges were laid, the issue really quieted down. There was no mention of it as to the name of the person charged, how many customers were effected, what happened to the person charged, or what the company did to better protect consumers, and what they are doing now to vet their employees who are in charge of and pos systems and how they are ensuring their customers information is safe at point of purchase.
Well, that’s the ultimate problem, isn’t it? How does the customer verify the POS? This kind of skimming is only possible because the authentication is one-way all the time (bank verifies customer is real, never the other way around…)
There should be a green LED on the customers’ card that lights up when the POS has authenticated itself to the card, before you enter your PIN.
Just pay in cash whenever you can. Also, keep sufficient amount of cash in wallet for a day.
Plan your shopping. (for Home, for Entertainment)
Prior that get equal amount of cash for each shopping.
OR
use separate accounts/cards for each shopping activity. (sub card for home shopping, gift cards for online shopping)
etc… etc…
Hope, this is helpful.
Also, using cash you can manage your budget easily. As you know how much you have in hand. So, the extra buy happens less. (e.g. Buy one get one free, unnecessary buying extra things, As you assume you’re paying with a card so no need to worry about payment)
Cash payment helps you to focus on necessary shopping.
Its also restrict your shopping addictivity, if you have one.
Unfortunately, the cost of fraud is already built into whatever you’re buying. So, as a consumer in the US, it is safer for you to pay with a credit card (zero liability) than it is to carry around a bunch of cash.
I’ve always paid by cash. I only use my bank card card for online purchases.
Given the odds that you’re NOT going to be mugged on any given day, unless you’re mugged on the day you’re taking cash to buy a car, it’s unlikely you’ll lose any significant amount of cash due to crime – unless you’re someone who likes waving a wad of bills around to impress women. 🙂
And if you are mugged, they’ll get your credit card, too.
This also applies if you’re pick-pocketed.
And you can always conceal any excess cash elsewhere on your person than your wallet, which is always a good idea. Buy a money belt.
It really is easier to pay by cash and it really does help you stay budgeted and avoid the excessive credit build up which is a serious problem in the US – and which is much more likely to happen to you than being robbed of cash.
You got that right RSH! 🙂
It’s funny how everybody is talking about the benefits of cash or cards, but nobody has mentioned the gross security/profiling implications of card use over cash. Cash is always better. Also, if there are power problems or any other thing affecting banks or electronics, cash will always have the advantage of availability.
It would be interesting to know if for example people who were affected by blackouts (and food shortages) due to Hurricane Sandy change their cash vs card habits, by the way. Also much harder to get skimmed if you don’t use your card often.
One addendum to Brian’s comment; many credit unions pay back your 4+% (whatever) purchase charges every month or quarter; so you are actually a chump for using cash in that instance. Because you can actually shop cheaper using a credit union cash card.
I do not recommend doing this for anything other than local purchases, of course. I already had a vendor who was cracked, lose my debit card number to a spammer who used it to buy command and control space on a disreputable hosting site; so he could get at least 3 months of server space to do his C&C dirty deeds until the next free ride on stolen credit to the next free hosting space.
So even if you get the good deal, you need to monitor that account for any anomalies to tag any suspicious debits to unknown sources. That way you can possibly stay under the 48 hour window of liability to any illicit charges and get them back. Your credit union may not recover the loss, but at least you will not lose.