Confidential Computing
Protect data in-use with Confidential VMs, Confidential GKE, Confidential Dataflow, Confidential Dataproc, and Confidential Space.
Secure your data by keeping it encrypted in use—while it’s being processed
Simple easy-to-use deployment that doesn't compromise on performance
Confidential collaboration while retaining data ownership
Benefits
Breakthrough in confidentiality
Breakthrough in confidentiality
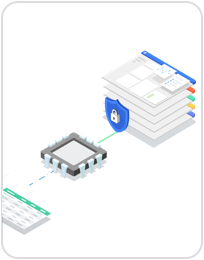
Confidential VMs are a breakthrough technology that allow customers to encrypt their data in the cloud while it’s being processed.
Simple for everyone
Simple for everyone
Google Cloud’s approach allows customers to encrypt data in use without making any code changes to their applications or having to compromise on performance.
Enabling new possibilities
Enabling new possibilities
Confidential Computing can unlock scenarios which previously have not been possible. Organizations are able to collaborate while preserving the confidentiality of their data.
Key features
Confidential Computing Platform
Confidential VMs
Confidential VMs can protect the confidentiality of data in the cloud by encrypting data-in-use while it’s being processed. Confidential VMs take advantage of security technologies offered by modern CPUs from AMD, Intel, and others. With Confidential Computing, customers can be confident that their data will stay private and encrypted even while being processed in the cloud. For AI/ML workloads on Intel, we also leverage Intel AMX, a CPU accelerator that is on by default on the general purpose C3 machine series for Confidential VMs. Confidential VMs on the C3 machine series brings hardware-level protection to your AI models and data and a significant performance boost for deep learning and inference workloads.
Confidential VMs with H100 GPUs
Confidential VMs on the accelerator-optimized A3 machine series with NVIDIA H100 GPUs can empower businesses to unlock the full potential of AI and machine learning while safeguarding sensitive data. Confidential VMs with H100 GPUs help ensure data remains protected throughout the entire processing pipeline, from the moment it enters the GPU to the moment the results are generated. This reduces the risk of unauthorized access, even by privileged users or malicious actors within the system. By providing a trusted execution environment for AI workloads, Confidential VMs on the A3 machine series allows businesses to collaborate more freely and securely with partners and third-party vendors.
Confidential GKE Nodes
With Confidential GKE Nodes, you can achieve encryption in-use for data processed inside your GKE cluster, without significant performance degradation. Confidential GKE Nodes are built on the same technology foundation as Confidential VMs. This feature allows you to keep data encrypted in memory with node-specific, dedicated keys that are generated and managed by the processor. The keys are generated in hardware during node creation and reside solely within the processor, making them unavailable to Google or other nodes running on the host.
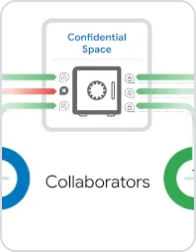
Confidential Space
With Confidential Space, organizations can gain mutual value from aggregating and analyzing sensitive data, all while maintaining the confidentiality of their data. Organizations can perform tasks such as joint data analysis and machine learning (ML) model training with trust guarantees that the data they own stays protected from all parties—including hardened protection against cloud service provider access. The Confidential Space integration with Privacy Sandbox provides a trusted execution environment and can be used to run privacy-preserving ad campaign analytics and remarketing in the post-cookie world.
Confidential Dataflow and Dataproc
Dataflow is a fully managed service that supports a wide range of streaming analytics and machine learning use cases at massive scale. With Confidential VMs support in Dataflow, you can process your data pipelines using Compute Engine Confidential VMs, which provide inline memory encryption.
Dataproc enables big data processing through fully managed Spark, Hadoop, and other open source tools and frameworks. With Confidential Dataproc you can create a Dataproc cluster that uses Compute Engine Confidential VMs to provide inline memory encryption. This furthers security guarantees, especially when processing highly sensitive data.
Customers
See how our customers are using Confidential Computing
What's new
What's new
Sign up for Google Cloud newsletters to receive product updates, event information, special offers, and more.
Documentation
Documentation
Confidential VM overview
Learn more about Confidential VMs, including support for end-to-end encryption, compute-heavy workloads, and more security and privacy features.
Create your first Confidential VM instance
Quickly get up and running with a new Confidential VM instance using default settings in the Google Cloud Console.
Try Confidential VM
Learn how to create a Confidential VM instance in an interactive tutorial.
Monitor Confidential VM integrity
Learn how to use Cloud Monitoring to monitor and validate the integrity of a confidential VM's OS, the integrity and version of the VM's SEV, and more.
Dataproc Confidential Compute
Learn how to create a Dataproc cluster that uses Compute Engine Confidential VMs to provide inline memory encryption.
Split-trust Encryption Tool
Learn how to accomplish unified control of data at-rest, in-use, and in-transit with ubiquitous data encryption and the Split-trust Encryption Tool.
Not seeing what you’re looking for?
All features
All features
| Real-time encryption in use | Google Cloud customers can encrypt data in use, taking advantage of security technology offered by modern CPUs from AMD, Intel, and others together with confidential computing cloud services. Customers can be confident that their data will stay private and encrypted even while being processed. |
| Lift and shift confidentiality | Our goal is to make Confidential Computing easy. The transition to Confidential VMs is seamless—all workloads you run today, new and existing, can run as a Confidential VM. You do not need to make any code changes to your applications to use Confidential VMs. One checkbox—it’s that simple. |
| Detection of advanced persistent attacks | Confidential Computing builds on the protections Shielded VMs offer against rootkit and bootkits. This helps ensure the integrity of the operating system you choose to run in your Confidential VM. |
| Enhanced innovation | Confidential Computing can unlock computing scenarios that have previously not been possible. Organizations will now be able collaborate on sensitive and regulated data in the cloud, all while preserving confidentiality. |
| High performance | Confidential VMs offer similar performance to standard N2D VMs. Explore tech docs and whitepapers. |
Pricing
Pricing
Pricing for Confidential VMs is based on usage of the machine types, persistent disks, and other resources that you select for your virtual machines.
A product or feature listed on this page is in preview. Learn more about product launch stages.
Take the next step
Start building on Google Cloud with $300 in free credits and 20+ always free products.
Need help getting started?
Contact salesWork with a trusted partner
Find a partnerContinue browsing
See all products