When investigating iOS devices, you may have seen references to the SoC generation. Security researchers and developers of various iOS jailbreaks and exploits often list a few iPhone models followed by a note that mentions “compatible iPad models”. This is especially common when discussing iOS forensics, particularly referring to the checkra1n jailbreak. What do those references mean, and how are the iPhone and iPad models related? Can we count the iPod Touch and Apple TV, too? Let’s have a look.
How to identify your model
This is the first step. Apple has detailed instructions:
The Apple Watch is missing here, though there is an article on them, too; the problem is that Apple Watch acquisition is very limited.
Usually it is as simple as that: check the back cover of the device (the iPhone, iPad or iPod Touch) and check the model number in the Axxxx format. The ‘xxxx’ are the four digits. Once you are done, search across the above-mentioned pages. Just note that some iPhone and iPod models may share the same external design, and sometimes the back cover is replaced with the one from a different model. The only reliable method is opening the [Settings] | [About] and checking the model.
SoC (Silicon on Chip)
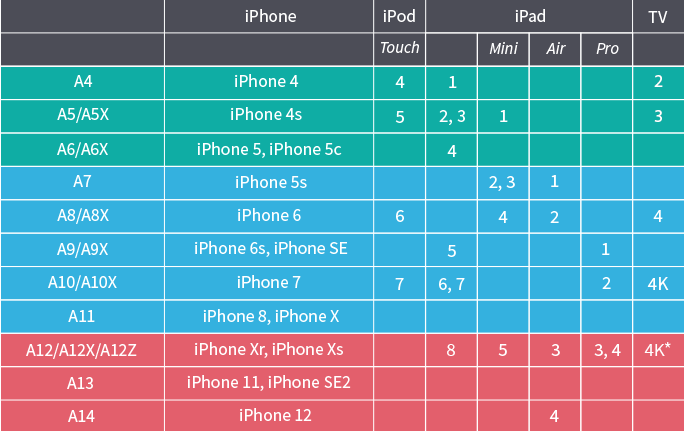
The heart of every Apple device is the SoC, or System on a chip. Apple uses ARM processors of its own design; the current one for now is A14, which appears in the iPad Air (2020). How does that affect the compatibility of available acquisition methods? Is that the only factor or there is something else except iOS version?
Let’s start with the SoC (CPU). We have collected information from public sources and compiled this information for you:

Noted the different colors? Here is the explanation.
- Green: you can do almost everything, including passcode cracking, and even perform BFU extractions (may be limited if the password is not known)
- Blue: devices vulnerable co checkm8 exploit. BFU (Before First Unlock) is possible regardless of iOS version, but the devil is in the detail (see below)
- Red: you cannot do anything with locked devices
BootROM exploit
The checkm8 exploit is the thing you might’ve already heard about. The exploit’s compatibility is difficult to grasp. The developers state that it is compatible with the iPhone 4s through iPhone X range of devices, but in fact the compatibility matrix is a bit more complex:
- Currently available SoC support: s5l8947x, s5l8950x, s5l8955x, s5l8960x, t8002, t8004, t8010, t8011, t8015
- Planned SoC support: s5l8940x, s5l8942x, s5l8945x, s5l8747x, t7000, t7001, s7002, s8000, s8001, s8003, t8012
Confused? No wonder. These IDs are actually bootrom versions. For example, the T8010 is the one used in the iPad 6th and 7th gen, iPhone 7 and 7 Plus, and iPod Touch 7th gen.

If you look at the checkra1n jailbreak, you might be confused even more. The release notes for the latest version read:
However, with the recently published blackbird vulnerability, we are able to get control of the Secure Enclave on A10 and A10X and disable this mitigation. Support for A10 and A10X devices is being worked on and is expected to be ready in the coming weeks.
The compatibility is described as follows:
- iPhone 6s, 6s Plus, and SE
- iPad 5th generation
- iPad Air 2
- iPad mini 4
- iPad Pro 1st generation
- Apple TV 4 and 4K
The list is weird. For example, the iPad mini 4 has the A8X SoC, which corresponds to that is used in the iPhone 6 and 6 Plus; however, the iPhone 6 cannot run iOS 14 (and even iOS 13), while the iPad mini 4 can.
Acquisition
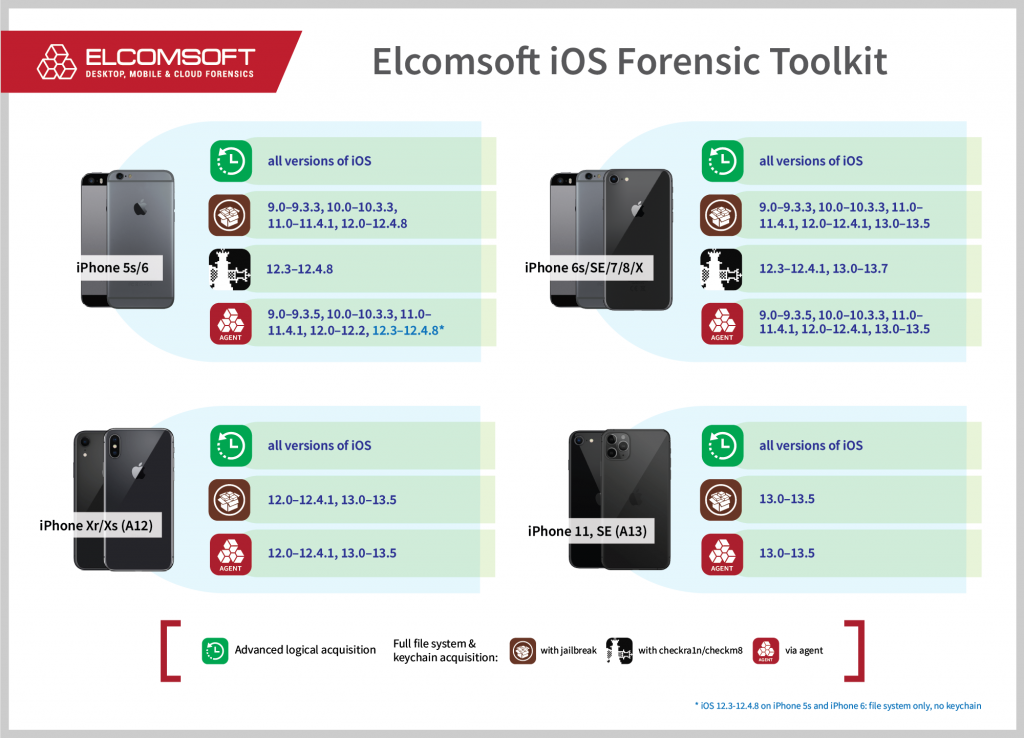
At the time of extracting the data, you may not care about device models, chipsets and iOS versions. You just need to get the job done, and if you are working as a forensic expert, all you need to know is the availability of various acquisition methods. This is the current availability matrix:

The matrix is in fact not complete. First, it misses some older devices such as the iPhone 4, 4s, 5 and 5c. Second, it does not include iOS 14 compatibility, which is now limited to iPhone 6s, iPhone SE, Apple TV and “compatible iPad models”, see above.
Summary:
- iPhone 4, iPhone 4s, iPhone 5, iPhone 5s: you can do virtually everything, even for locked iPhones
- iPhone 6s to iPhone X: full file system and keychain acquisition for iOS up to 13; partial acquisition (BFU) if the passcode is not known
- iPhone 6s and SE: the above is applicable for iOS 14 as well
- iPhone Xr/Xs and iPhone 11: file system and keychain acquisition for iOS 13.5 and below, but only if the passcode is known
Use Elcomsoft iOS Forensic Toolkit as this is the only tool you need to perform the full file system and keychain acquisition for jailbroken or compatible non-jailbroken devices.

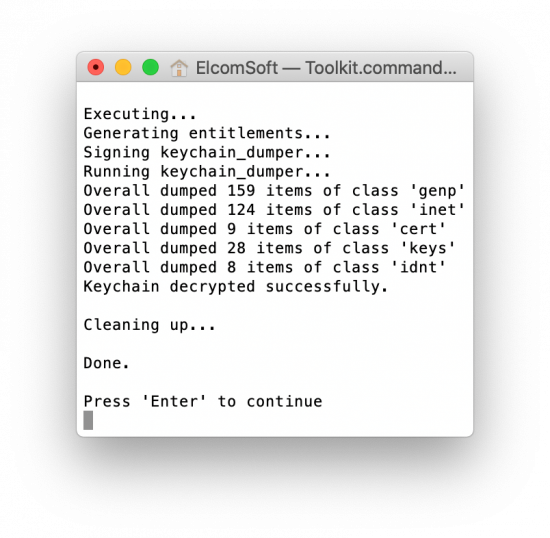
The above screen shot is for BFU acquisition (i.e. from the device with unknown passcode), by the way.
Other options
iCloud acquisition is a life saver. No matter which model iPhone you are extracting and what version of iOS it runs, if you have the user’s authentication credentials, you can download device backups, files from the iCloud Drive and quite a lot of synced data including account information, the usual categories like contacts, notes and iCloud Photos, as well as “end to end encrypted” data like iCloud keychain, messages (iMessage and SMS), Health and much more. The tools? Elcomsoft Phone Breaker, the only product on the market that can download all of that data.

checkm8, checkra1n, EIFT, Elcomsoft iOS Forensic Toolkit, Elcomsoft Phone Breaker, Elcomsoft Phone Viewer, EPB, EPV, iCloud, iOS, iOS 14, iOS14, iPad, iPhone, keychain