The post Ecommerce Security Incidents: Stripe, Pandora, and OpenCart appeared first on RapidSpike.
]]>Here are three recent incidents making headlines, and what they mean for ecommerce operators.
1. Stripe Phishing Scams
Stripe has warned merchants and customers about a surge in phishing campaigns. Attackers are sending fake emails and texts, often claiming urgent account issues, that lead to spoofed Stripe login pages. Once credentials are entered, the attackers can access funds or hijack payment gateways.
Even if your systems are secure, a single employee duped by a phishing email can compromise payment accounts. Merchants should train staff to:
- Verify that Stripe emails only come from @stripe.com domains.
- Double-check URLs before logging in.
- Use two-factor authentication on all Stripe accounts.
2. Pandora’s Third-Party Data Breach
Jewelry brand Pandora confirmed a data breach that exposed customer names and email addresses. The breach was traced to a third-party vendor, not Pandora’s own servers.
This incident highlights one of the biggest risks in ecommerce today, vendor and integration security. Even if you lock down your own environment, customer data may be exposed through a plugin, CRM, or other third-party tool. Ecommerce owners should:
- Audit third-party services regularly.
- Get alerts when a new third-party is added.
- Limit the customer data they share with external platforms.
3. OpenCart Malware Campaign
Security researchers uncovered a large-scale attack targeting OpenCart stores. Thousands of sites were infected with obfuscated JavaScript posing as analytics tags. The malware replaced checkout forms with fraudulent versions, silently stealing customers’ credit card details.
This is a classic web-skimming attack, and one of the most damaging to customer trust. Once word spreads that a store has leaked payment data, the reputational fallout can be catastrophic. Merchants should:
- Keep ecommerce platforms and plugins patched.
- Monitor checkout pages for unauthorised code.
- Use tools that validate third-party scripts in real time.
Why Ecommerce Stores Are Being Targeted
- Attackers follow the money: Checkout pages and customer data are prime targets.
- Third-party risk is rising: Many breaches now start with vendors, not merchants directly.
- Phishing is effective: Even security-minded staff can be tricked by convincing emails.
- Malware is stealthy: Campaigns like the OpenCart attack are designed to evade detection for months.
Stay Vigilant with CartShark
CartShark by RapidSpike helps ecommerce businesses monitor their scripts and third-party integrations, giving merchants better visibility into hidden risks. CartShark adds a vital layer of defense in an increasingly hostile threat landscape.
Attackers aren’t slowing down, the time to act is now. Protect your store, your customers, and your reputation, make vigilance part of your ecommerce strategy today.
The post Ecommerce Security Incidents: Stripe, Pandora, and OpenCart appeared first on RapidSpike.
]]>The post Introducing CartShark 🦈 appeared first on RapidSpike.
]]>RapidSpike is proud to introduce CartShark, a revolutionary cybersecurity platform that empowers ecommerce businesses to combat these threats swiftly and effectively.
A New Era in Ecommerce Security
CartShark represents a leap forward in protecting online stores from web-skimming attacks. By combining Real User Data and Synthetic User Data, CartShark detects and alerts you to unauthorised data exfiltration, giving you the tools to act quickly. It’s not just about protecting customer data; it’s about safeguarding your brand’s reputation in an increasingly competitive market.
Why CartShark?
Developed by the security experts at RapidSpike, CartShark is designed to provide unparalleled insights and control over your ecommerce website. With the ability to identify Magecart attacks in minutes rather than months, your ultimate ally in the fight against cybercrime.
Here’s how CartShark is changing the game:
Real User Monitoring
CartShark provides actionable insights by analyzing real customer interactions. This enables businesses to detect unusual patterns or unauthorised scripts that may signal a web-skimming attack. Understanding how your site operates under actual usage conditions is critical to preempting potential threats.
Synthetic Monitoring
By simulating critical user journeys, CartShark proactively identifies and resolves vulnerabilities before they impact real users. Synthetic monitoring also uncovers hidden skimming scripts, ensuring no stone is left unturned in your security efforts.
Third Party Monitoring
External scripts are often exploited as entry points for web-skimming attacks. CartShark’s third-party monitoring tracks and manages these integrations, alerting you to unauthorised changes or malicious scripts in your supply chain.
AI-Driven Insights
Complexity is the enemy of efficiency. CartShark leverages AI-driven analysis and remediation to simplify cybersecurity, delivering automated reporting and actionable insights to your team.
Recognised Innovation
CartShark’s revolutionary approach has been acknowledged with the prestigious Innovate UK Smart Grant. This recognition highlights its potential to transform the ecommerce security landscape. Already trusted by leading global retailers, CartShark is proving its value by delivering enhanced visibility and control.
Trusted by Industry Leaders
CartShark builds on RapidSpike’s existing Magecart Detection tool, providing even greater capabilities to tackle modern threats. Caleb Whittington, Security Engineer at Kurt Geiger, describes it as “fantastic for website security, as it provides full visibility of all data sources across each of Kurt Geiger’s websites – a problem we previously needed to solve.”
A Message from Our CEO

“At CartShark, we know that ecommerce brands—big and small—work tirelessly to create seamless shopping experiences for their customers. With the growing threat and sheer volume of web-skimming attacks and sophisticated data exfiltration attacks like Magecart, protecting checkout pages and personal data has never been more critical.
Introducing our newest product CartShark—designed specifically to give businesses of all sizes the visibility, speed, and confidence they need to defend against these types of cyber threats. By detecting and alerting to malicious activity and identifying 3rd party vulnerabilities in real time, CartShark ensures that your customers’ payment and personal data stays secure keeping your brand’s reputation intact.
We’re excited to help ecommerce brands stay ahead of the threats, stay compliant, and stay secure.”
An Exciting Road Ahead
With a customer-driven product roadmap, the platform is constantly evolving to meet the challenges of modern ecommerce. From addressing emerging threats to enhancing usability, CartShark is committed to making online shopping safer for businesses and consumers alike.
See CartShark in Action
Discover how CartShark can transform your ecommerce security strategy. Watch a demo today and take the first step towards a safer, more secure online store.
Protect your website. Protect your customers. Protect your reputation.

The post Introducing CartShark 🦈 appeared first on RapidSpike.
]]>The post Intelligent Alerting with RapidSpike and ilert Integration appeared first on RapidSpike.
]]>That’s where ilert comes in. By integrating RapidSpike with ilert, you can easily transform monitoring alerts into incidents, leading to quicker response times, enhanced team collaboration during downtime, and better communication with stakeholders and clients.
Why Integrate RapidSpike with ilert?
RapidSpike provides powerful monitoring for website uptime, performance, and security. It ensures you stay ahead of potential issues by identifying slow response times, downtime, and cybersecurity vulnerabilities. However, receiving an alert is only the first step, managing and responding to those alerts effectively is crucial.
By integrating with ilert, you can:
- Reduce alert fatigue – Intelligent alerting prevents unnecessary notifications.
- Automate incident response – Assign alerts to on-call teams based on escalation policies.
- Improve response times – Ensure incidents are resolved faster with structured workflows.
- Gain visibility – Track and analyse historical incidents for long-term reliability improvements.
How the Integration Works
Once RapidSpike detects an issue, it automatically triggers an alert to ilert. ilert then applies intelligent routing, notifying the right personnel via multiple channels (SMS, phone calls, push notifications, and integrations like Slack and Microsoft Teams).
If an alert isn’t acknowledged, ilert escalates the incident according to predefined schedules, ensuring that no issue goes unnoticed.
The integration between RapidSpike and ilert ensures that businesses can monitor, alert, and respond to incidents in real time. By combining proactive monitoring with smart alerting and escalation, this integration helps teams minimise downtime, improve website reliability, and deliver a seamless user experience.
If you haven’t set up the ilert integration yet, now is the perfect time to enhance your incident management strategy. Follow this guide and experience the benefits of proactive monitoring with intelligent alerting.
The post Intelligent Alerting with RapidSpike and ilert Integration appeared first on RapidSpike.
]]>The post Casio UK Hit With Payment Skimming Attack appeared first on RapidSpike.
]]>
Image Source: Casio UK Website
What is a Web Skimming Attack?
Web skimming, also known as formjacking or Magecart attacks, involves injecting malicious JavaScript code into websites, particularly ecommerce platforms, to steal sensitive user data during transactions. Attackers typically target payment pages to capture information such as credit card numbers, billing addresses, and contact details. This intercepted data is then transmitted to external servers controlled by the attackers and sold on the dark web.
Attack Analysis
Unlike traditional skimming attacks that focus solely on checkout pages, this incident employed a two-stage skimmer active across all website pages except the checkout page. The attackers exploited known vulnerabilities in the Magento ecommerce platform, executing a two-tier skimming operation that allowed them to exfiltrate data stealthily.
The initial stage involved an unobfuscated loader disguised as a legitimate third-party script. This script acted as a gateway for the secondary payload. This loader then triggered a more advanced skimmer that was deployed to encrypt and exfiltrate sensitive data, including contact information, credit card details, and billing addresses. To avoid detection, the attackers used XOR-based string masking and custom encoding techniques, making the malicious script harder to identify.
The skimmer was active on Casio UK’s website from January 14th to 24th, 2025, remaining undetected for ten days. Casio remediated the issue on January 28th, 2025, after being alerted to the breach. However, the total number of affected customers remains unknown.
Preventative Measures
To mitigate the risk of web skimming attacks, ecommerce businesses should implement the following security measures:
- Regular Security Audits: Conduct frequent vulnerability assessments and penetration testing to identify and resolve potential security gaps.
- Third-Party Script Management: Carefully vet and continuously monitor third-party scripts and services to prevent unauthorized code injections.
- Content Security Policy (CSP): Enforce a strict CSP to limit the execution of unauthorized scripts, reducing the risk of code injection attacks.
- Magecart Detection: Deploy advanced monitoring solutions that can detect and block unauthorized scripts in real time, ensuring a rapid response to security threats.
The Casio UK breach underscores the growing sophistication of web skimming attacks and the need for proactive cybersecurity measures to protect consumer data. As threat actors continue to evolve their techniques, ecommerce businesses must stay vigilant and prioritise security to safeguard customer trust and financial information.
The post Casio UK Hit With Payment Skimming Attack appeared first on RapidSpike.
]]>The post Magecart Attack: ‘Temporarily Out Of Orbit’ appeared first on RapidSpike.
]]>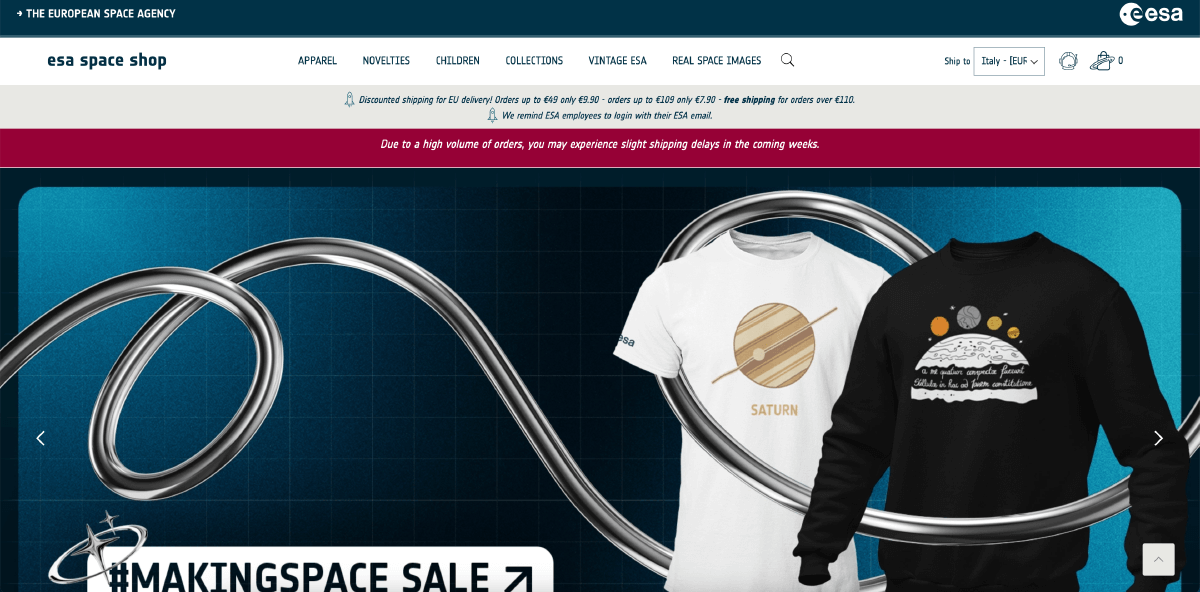
Image Source: ESA Website
Domain Spoofing
The attackers employed a technique known as domain spoofing. Domain spoofing is a commonly used tactic by attackers to evade detection. It has been observed in several high-profile Magecart attacks over the years, such as the British Airways breach, where a malicious skimmer siphoned card details to a fake domain, ‘baways[.]com’.
The ESA hackers created a deceptive domain, “esaspaceshop.pics,” closely resembling the legitimate “esaspaceshop.com.” This malicious domain hosted the fake payment page, which was served to customers during the checkout process. The counterfeit page mimicked the appearance of a legitimate Stripe payment interface, making it difficult for users to detect the fraud.
The injected script contained obfuscated HTML code derived from the legitimate Stripe Software Development Kit. This obfuscation concealed the malicious intent, allowing the fake payment page to collect sensitive customer information, including payment card details, without raising suspicion.
Fake Payment Gateways
The breach was identified on December 24, 2024 as the malicious script was actively collecting customer data. Several security firms confirmed these findings, capturing live instances of the fake Stripe payment page being presented to customers.
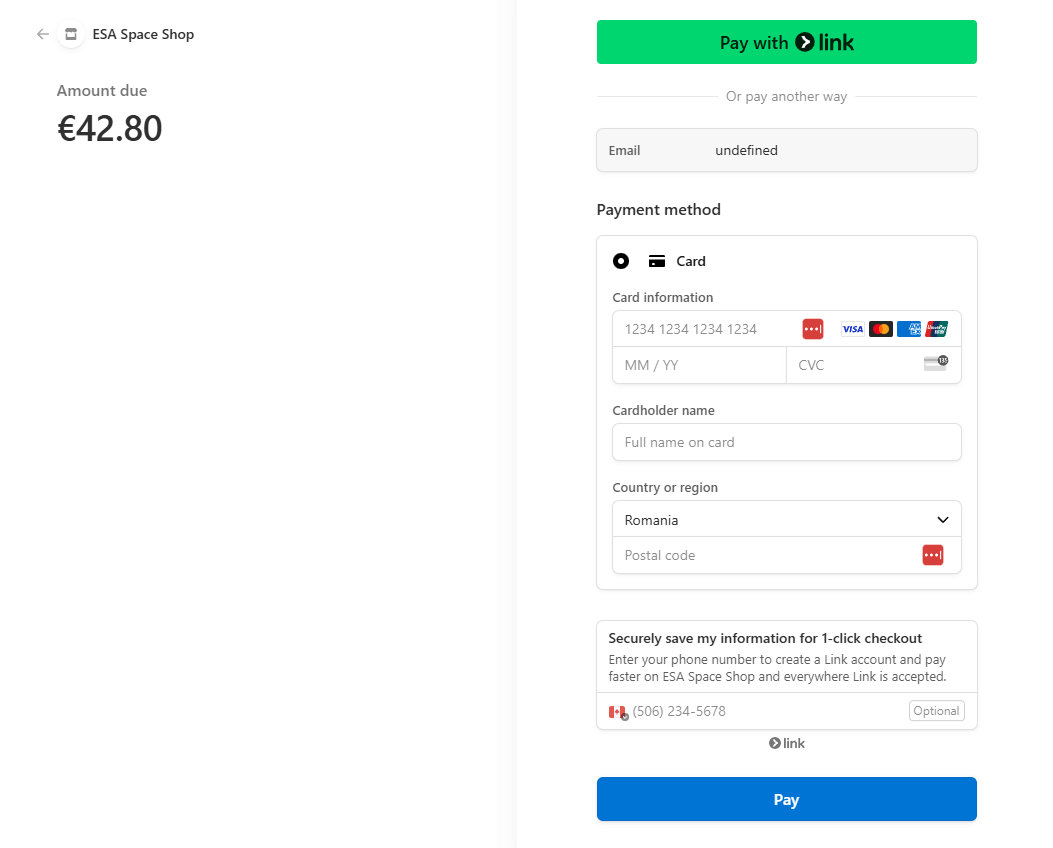
Image Source: Bleeping Computer, 2024
Upon discovery, the ESA took the online store offline, displaying a message indicating that the site was “temporarily out of orbit.”, a pun, despite the reality being much more serious. The agency clarified that the store was managed by a third-party vendor and not hosted on ESA’s infrastructure. This distinction suggests that the breach was confined to the online store and did not affect ESA’s internal systems. It its not yet known how long the attack took place or how many customers were impacted.

Image Source: Forbes, 2024
Magecart Detection Recommendations
This incident underscores the importance of robust security measures for ecommerce websites, especially those managed by third-party vendors. Domain spoofing and the injection of malicious scripts are common tactics used by cybercriminals to steal sensitive information.
To mitigate such risks, ecommerce stores should consider the following measures:
- Regular Security Audits: Conduct comprehensive security assessments of all web applications, plugins and associated third-party services to identify and address vulnerabilities.
- Magecart Detection: Deploy monitoring tools to continuously trace through a website to detect unusual activities, such as unauthorised script injections or domain spoofing attempts.
By implementing these measures, organisations can enhance the security of their online platforms and protect customers from similar cyber threats.
The post Magecart Attack: ‘Temporarily Out Of Orbit’ appeared first on RapidSpike.
]]>The post The Biggest Ecommerce Challenges this Black Friday appeared first on RapidSpike.
]]>As ecommerce continues to outdo the high street, Black Friday sales are becoming as much of a tradition as Christmas dinners. But shoppers are very influenced by external factors, from the economy to website experiences.
We outline the key ecommerce challenges this Black Friday…
Customers are spending less or shopping around
The elephant in the room for most retailers is the cost-of-living crisis. In a recent YouGov study, it was revealed that six in 10 consumers are planning to spend less this year. Non-essentials have taken a back seat as shoppers struggle to make ends meet with inflation and energy bills.
According to the State of Living Report, 72% of shoppers say they’re planning to cut back on luxuries. This is particularly worrying for upmarket brands, as the report also suggests that 58% of shoppers will seek discount retailers.
On the plus side, money-conscious customers may be more interested in getting a good deal. Those who can offer the biggest discounts, in tandem with a seamless website experience, may therefore come out on top.
Much of this comes down to website loading speed. In one eye-opening case study, a headphone retailer was found to be losing as much as £2.5 million per year simply due to poor performance. The takeaway? Improve your website or risk the consequences.
Payment scams are on the rise
Of course, a seamless website experience doesn’t come down to the transaction alone. Security also plays a huge part in customer confidence loyalty, and one of the lasting effects of the pandemic was the increase in online payment scams.
Between 2020 and 2021, cases of online fraud rose by 33%. These included payment interception, whereby hackers impersonated company representatives to send customers to fake payment pages. More sophisticated attacks included intercepting cardholder data as customers made their way through the checkout process.
Conversely, merchants also felt the sting in the form of refund fraud. Hackers would purchase items, then claim they had no knowledge of placing the order, only to log a dispute and keep the goods. According to the National Retail Federation, for every $100 of merchandise returned, $10.30 is lost to fraud.
Slow websites are losing sales
The headphone retailer case study above is just one example of customers’ high expectations. Another consequence of the pandemic, shoppers’ patience is wearing thin with slow websites. According to Kissmetrics, almost half (47%) of customers expect a website to load within 2 seconds.
Even more sobering, 88% of shoppers would leave a website after a bad experience, and a 1-second delay could cause conversions to drop by 7%. But the good news is that many of these issues are easily detectable, and fixable.
Tools like Google Lighthouse analyse individual URLs and highlights issues in accessibility, SEO and performance. Core Web Vitals, meanwhile, puts user experience first. Testing for issues like ‘cumulative layout shift’ (the movement of elements on a page), it shows retailers where their sites may not be performing as they should.
Web skimming attacks are rife during promotional periods
While payment scams are generally higher right now, web skimming attacks peak during periods like Black Friday. Bearing in mind that 95% of all cyber breaches stem from human error, retailers should be aware of:
- Magecart – stealing customer data from forms by exploiting web server vulnerabilities
- Fake checkouts – forms appearing before the real checkout page
- Domain spoofing – impersonating transactional websites.
Prevention is better than the cure here, with penetration tests and vulnerability scans offering assurance. But in the event of an attack, it’s essential to keep customers informed. A five-step plan of investigation, informing ICOs, informing customers, monitoring reinfection and protecting customers, could prevent reputational damage.
The takeaways
As with any retail experience, looking after the customer should always be a top priority. Online vendors should prepare for security breaches this Black Friday, while also monitoring website performance to ensure customers can access much-needed discounts.
With the right preventative measures, retailers can protect their reputation and maintain stable sales throughout the year – not just at Christmas.
The post The Biggest Ecommerce Challenges this Black Friday appeared first on RapidSpike.
]]>The post The Cisco Magecart Attack appeared first on RapidSpike.
]]>Get Started With Free Magecart Detection
Understanding Magecart Attacks
Magecart also known as web skimming attacks, are not a single group but rather a collective of various cybercriminal groups that exploit vulnerabilities in websites for financial gain. These attackers often insert malicious JavaScript code into web pages to intercept payment card data during the checkout process. This intercepted data is then transmitted to external servers controlled by the attackers and sold on the dark web.
Magecart Attack Execution
Attackers utilised several methods to execute the Magecart attack:
- Vulnerabilities: The attackers gain access to the ecommerce site, exploiting vulnerabilities within the site’s code. Common entry points include outdated plugins, insufficient access controls or marketing tools.
- Injection of Malicious Code: Once the attackers have access, they inject a malicious JavaScript snippet directly into the checkout pages. This code is designed to capture credit card details, billing information, and other sensitive data entered by users.
- Data Exfiltration: The stolen data is then sent to remote servers, often using obfuscation techniques to hide the true nature of the outbound traffic.
The Cisco Magecart Incident
On 1st September 2024, Cisco faced a security breach as a result of a Magecart attack, specifically targeting the checkout processes on the merchandise website. This incident not only affected the security of customer data but also raised concerns about the security of the enterprise-level solution.
Discovery and Mitigation
Cisco’s merchandise store is currently offline due to a security incident involving harmful JavaScript code intended to steal sensitive customer information during the checkout procedure. Anonymous researchers have suggested that this breach may be associated with a CosmicSting attack (CVE-2024-34102).
While the specifics of the intrusion are still unclear, it is believed that the malicious JavaScript was injected into the website over the weekend of August 30th. The heavily obfuscated code gathers sensitive information, including credit card details, postal addresses, phone numbers, email addresses, and user login credentials. The malicious JavaScript is highly obfuscated and was delivered from the domain rextension.[net], which was newly registered on August 30.
CosmicSting, a security threat, that affects the Adobe Commerce (Magento) platform, allows attackers to perform XML external entity (XXE) injections, enabling them to insert harmful code into content management system (CMS) blocks within the checkout process.
On September 5th, 2024, a Cisco spokesperson provided the following statement for BleepingComputer:
“We are aware of an issue related to a Cisco-branded merchandise website that’s hosted and administered by a third party supplier. The site has been temporarily taken offline as a precaution while we address the issue, and we are notifying the limited number of site users that we identified as having been impacted by the issue. No employee credentials have been compromised.”
Preventative Measures
Organisations can take proactive measures to fortify their defences against attacks:
- Regular Security Audits: Conduct frequent security assessments to uncover vulnerabilities.
- Security Awareness Training: Regular training for employees regarding phishing and other social engineering attacks can help reduce the likelihood of an initial breach.
- Content Security Policy (CSP): Implementing a robust CSP can limit the execution of unauthorised scripts, reducing the risk of code injection attacks.
- Magecart Detection: Leverage advanced monitoring solutions that can quickly identify untrusted scripts to enable rapid response to breaches.
The Cisco Magecart attack serves as a stark reminder of the persisting threats within the ecommerce domain. Organisations must stay vigilant and adopt a comprehensive approach to cybersecurity, encompassing prevention, detection, and response strategies.
As cybercriminals continue to refine their methods, the responsibility lies with businesses to safeguard their platforms and protect sensitive customer information from exploitation. Staying informed and prepared is the best defence against the ever-present threat of Magecart and other cyberattack vectors.
Get Started With Free Magecart Detection
The post The Cisco Magecart Attack appeared first on RapidSpike.
]]>The post RapidSpike Awarded Innovate UK Smart Grant for AI Website Monitoring Platform appeared first on RapidSpike.
]]>Innovate UK, part of UK Research and Innovation, has allocated up to £25 million to support groundbreaking innovations with exceptional potential for commercial success. RapidSpike’s plans for its AI website monitoring platform has been recognised as a responsible and standout project in this regard.
RapidSpike’s AI website monitoring platform aligns perfectly with the Smart grant’s focus, offering a revolutionary approach to website performance monitoring that harnesses the huge amount of data collected by RapidSpike, whilst removing all complexity around configuration and data delivery. The platform will include AI analysis and remediation, third party tracking, data breach protection, self-healing User Journeys, and more.
“We are thrilled to receive the Innovate UK Smart grant, which reaffirms the groundbreaking plans for our AI-driven website monitoring platform,” said Matt Waters, CEO of RapidSpike. “As digital commerce continues to evolve, we remain committed to adapting our offerings to meet the new needs of businesses. This grant will enable us to accelerate the development of our AI engine, further aiding our aim to help create faster, safer and more reliable websites for everyone. We’d like to thank Innovate UK for supporting us in this exciting opportunity.”
The application process for the Innovate UK Smart Grant is rigorous, and successful applicants had to demonstrate plans that achieved return on investment and market share growth. RapidSpike’s proposal stood out for its unique technological advancements and its robust, realistic plans for achieving tangible returns.
RapidSpike’s plan involves leveraging millions of data points in partnership with advanced artificial intelligence algorithms to provide ecommerce businesses of all sizes with unparalleled insights into their website, empowering them to optimise user experience, enhance security, and maximise website conversions. By combining cutting-edge technology with user-centric design, RapidSpike is poised to revolutionise the way ecommerce websites monitor and manage their online presence.

RapidSpike Leadership Team
The post RapidSpike Awarded Innovate UK Smart Grant for AI Website Monitoring Platform appeared first on RapidSpike.
]]>The post New Features to Meet Upcoming Ecommerce Security Regulations appeared first on RapidSpike.
]]>We recently featured in Prolific North. If you missed the write up, you can catch up in full, here…
In response to rising ecommerce threats, the Payment Card Industry Data Security Standards will impose 63 new requirements on brands processing, storing or transmitting credit card information, with version 4.0 coming into effect on March 31, 2025.
While industry think tanks are warning that some businesses are leaving it too late to prepare, RapidSpike has bolstered the functionality of its award-winning website monitoring platform with thousands of new data points to support retailers with the transition.
Among the new releases is a PCI compliance dashboard with the ability to track all script files found on an ecommerce site, with an inventory displaying where they were detected and the last time they were seen, so they can be effectively managed. A content security policies dashboard will also safeguard the authorisation of each script, with advice given to remedy errors in-line with the threat level.
Wider innovations from RapidSpike’s Leeds technology hub include new functionality to manage website third parties including live chats, support plugins, analytics, payment gateways, and postcode lookups. While such third parties are often deemed essential for running successful ecommerce sites, they can create costly security, speed, usability and reliability issues. RapidSpike’s new diagnosis panel provides greater insight into the third party data uncovered throughout the app, to supercharge customers’ ability to make adjustments — whether reducing load times or removing third parties entirely if the integrity of a site is compromised.
“From automotive retailers to travel operators, and fashion stores to FMCG sites, all of these brands are facing tougher times when it comes to transacting online,” explained RapidSpike’s CEO Gav Winter. “We only have to monitor mainstream headlines to see how prevalent Magecart-style ‘form-jacking’ attacks are becoming, and the cost and reputational damage of these payment theft breaches is astronomical. Margins are also being squeezed, and competitive pressures are rising.
“We are here to continually empower our ecommerce customers with greater insight into their website health — whether that’s to aid compliance, safeguard reputation, or boost revenues. That’s why we’ve released three new features in the last six months alone.”
A new return on investment calculator has been built, to predict the revenue impact of website tweaks, including page performance, accessibility, and downtime improvements.
Wider new releases have also been unveiled to make RapidSpike more intuitive, including a setup wizard to accelerate the monitoring process, website switcher for customers monitoring multiple URLs, and the ability to compare a website’s performance against RapidSpike’s new ‘Baseline’ indicator of all stats across every customer account.
The post New Features to Meet Upcoming Ecommerce Security Regulations appeared first on RapidSpike.
]]>The post Managing Website Design and User Experience appeared first on RapidSpike.
]]>We recently featured in Ecommerce Age. If you missed the write up, you can catch up in full, here…
There’s no doubting the incredible power that a well-designed ecommerce website can wield. Imagine the intricate detailing of a high-res product image showcasing every groove in a brand-new bike tyre. Put yourself into the shoes of the buyer as those boots illuminate the fashion model. From single product images to hero banners lighting up category pages, there’s a lot to be said for design. But things have come a long way in recent years: page elements are heavier, rendering pages slower. And when 1 second of page delays leads to a 7% decrease in conversions, it’s time to panic.
Where design and user experience overlap
Enter, the new and improved approach to web design: user experience. Certainly, there’s nothing new about giving our customers the best level of service possible. But we are seeing this play out in a big way in the digital sphere – whether that’s Google’s Core Web Vitals or simply optimising for mobile experiences.
The four key factors for a well-performing ecommerce website
It’s a myth that developers and designers are interested in aesthetics alone. Instead, they should focus on:
- Website speed
- Mobile responsiveness
- Security
- Accessibility.
Only with a holistic approach can retailers avoid critical cart abandonment issues or other user experience setbacks. Worse still, we run the risks of damaging the business if we don’t take this approach:
Loss of loyal customers
Brand loyalty means a lot more in brick-and-mortar stores than it does online. We might feel a sense of loyalty towards our closest supermarket or local boutique, but online, there are no geographical constraints. According to Hubspot, 88% of users said they wouldn’t return to a website if they had a bad experience.
Damage to brand reputation
A positive user experience lies in a simple user journey and a secure one. Our customers must feel confident that they can purchase safely – without the threat of attacks like Magecart. According to Ping Identity, 81% of customers would stop interacting with a brand online after a data breach.
Ecommerce sites are vulnerable to formjacking attacks wherein hackers can steal credit card details. It’s our job as user experience professionals to keep our cybersecurity in check.
Lower revenue
Lower revenue doesn’t just come from a loss of sales. Acquisition is far costlier than retention, so while we may lose out on those loyal customers, we might also get less from existing ones. A poor user experience – for example, a webpage failing to load products correctly – could reduce average order values. We may also be missing out on upselling and cross-selling opportunities.
How can we guarantee the Big 4?
To avoid these risks and assure faster, more responsive, secure and accessible websites, we turn to monitoring tools. Each of these ‘Big 4’ comes under the realm of website performance, so we can take a preventative and proactive stance.
Speeding up websites with page speed monitoring
A page speed monitoring tool identifies crucial errors that could be slowing down a site. It tracks every downloaded element from Javascript to image files, as well as cookie logs to identify what might be blocking content.
Testing mobile responsiveness for cross-device selling
Synthetic user journey monitoring can get into our users’ mindsets. This helps us to visualise what steps they might be taking to make a purchase, including categorising by device type. We may spot issues that show up on a mobile but not on a desktop, such as vital text or call to action buttons not working.
Monitoring malicious activity for formjacking attacks
In the UK, there are almost 5,000 formjacking attacks on transactional sites every month. These involve hackers exploiting security vulnerabilities and inserting malicious code into a web application. This code can integrate key-logging tools to copy users’ credit card and other details.
A Magecart detection tool stops these attacks in their tracks, monitoring suspicious activity and sending alerts to webmasters.
Adhering to user accessibility principles
Each industry will have its own set of accessibility standards – making sure users who are visually or otherwise impaired can access content. We can audit our websites for digital service standards or take advice from the Government’s accessibility guidelines.
Factors such as alt text, contrasting colours and optimisation for mobile devices will ensure our content is accessible to everybody.
Looking the part is just the beginning
A shop window may bring the customers in, but it’s the experience they’ll remember. By adhering to these principles, we can all optimise our user experience, prevent revenue loss, maintain our reputation and increase sales.
The post Managing Website Design and User Experience appeared first on RapidSpike.
]]>