-
A Novel Two-Level Protection Scheme against Hardware Trojans on a Reconfigurable CNN Accelerator
-
Evaluating the Security of Merkle Trees: An Analysis of Data Falsification Probabilities
-
Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs
-
A Note on the Quasigroup of Lai–Massey Structures
Journal Description
Cryptography
Cryptography
is an international, scientific, peer-reviewed, open access journal on cryptography published quarterly online by MDPI.
- Open Access— free for readers, with article processing charges (APC) paid by authors or their institutions.
- High Visibility: indexed within Scopus, ESCI (Web of Science), dblp, and other databases.
- Journal Rank: JCR - Q2 (Computer Science, Theory and Methods) / CiteScore - Q1 (Applied Mathematics)
- Rapid Publication: manuscripts are peer-reviewed and a first decision is provided to authors approximately 23.9 days after submission; acceptance to publication is undertaken in 3.7 days (median values for papers published in this journal in the first half of 2024).
- Recognition of Reviewers: reviewers who provide timely, thorough peer-review reports receive vouchers entitling them to a discount on the APC of their next publication in any MDPI journal, in appreciation of the work done.
Impact Factor:
1.8 (2023);
5-Year Impact Factor:
2.1 (2023)
Latest Articles
Implantable Medical Device Security
Cryptography 2024, 8(4), 53; https://doi.org/10.3390/cryptography8040053 - 15 Nov 2024
Abstract
Implantable medical devices, or IMDs for short, are medical instruments that are placed into the human body through surgery. IMDs are typically used for treating chronic diseases. Currently available IMDs are capable of communicating using wireless channels with other devices, either in close
[...] Read more.
Implantable medical devices, or IMDs for short, are medical instruments that are placed into the human body through surgery. IMDs are typically used for treating chronic diseases. Currently available IMDs are capable of communicating using wireless channels with other devices, either in close proximity or even connected to the Internet, making IMDs part of the Internet of Medical Things. This capability opens the possibility of developing a wide range of services, like remote patient data control, localization in case of emergency, or telemedicine, which can improve patients’ lifestyle. On the other hand, given the limited resources of such tiny devices, and the access to the Internet, there are numerous security issues to be considered when designing and deploying IMDs and their support infrastructures. In this paper, we highlight security problems related to Internet-connected IMDs, and survey some solutions that have been presented in the literature.
Full article
(This article belongs to the Special Issue Emerging Topics in Hardware Security)
►
Show Figures
Open AccessArticle
An Anonymous Authenticated Key Agreement Scheme for Telecare Medical Information Systems
by
Ghassan Hameed Faraj, Kamal Shahtalebi and Hamid Mala
Cryptography 2024, 8(4), 52; https://doi.org/10.3390/cryptography8040052 - 13 Nov 2024
Abstract
►▼
Show Figures
With the rapid development of information technology from one side and the experience of the COVID-19 pandemic from the other side, people presently prefer to access healthcare services remotely. Telecare Medical Information System (TMIS) provides more flexible, faster, and more convenient e-healthcare services
[...] Read more.
With the rapid development of information technology from one side and the experience of the COVID-19 pandemic from the other side, people presently prefer to access healthcare services remotely. Telecare Medical Information System (TMIS) provides more flexible, faster, and more convenient e-healthcare services available to all people, particularly those who lack access to physicians due to their geographical restrictions. However, due to the sensitivity of medical information, preventing unauthorized access to patient data and preserving patient privacy is crucial. In this paper, we propose an authenticated key agreement scheme for TMIS to preserve the privacy of the patient’s identity from all internal (even the health server and the physician) and external entities. Moreover, the physician’s identity is kept secret from all external entities. Formal and informal security analysis of the proposed scheme indicates that it is secure against all attacks in the context.
Full article
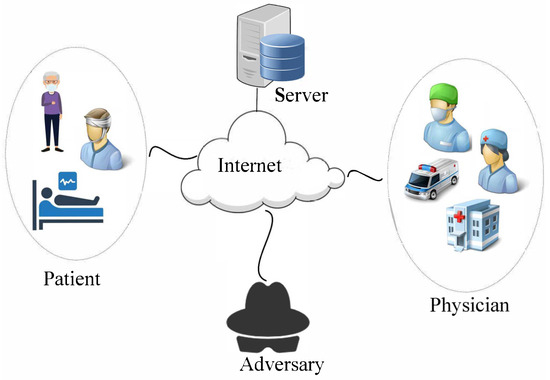
Figure 1
Figure 1
<p>Overview of the remote health care system.</p> Full article ">Figure 2
<p>Registration of a physician at the gateway.</p> Full article ">Figure 3
<p>Registration of a patient at the supervisor.</p> Full article ">Figure 4
<p>Registration of a supervisor at the gateway.</p> Full article ">Figure 5
<p>General architecture of the proposed authenticated key agreement scheme including main steps.</p> Full article ">Figure 6
<p>Authentication and session key generation.</p> Full article ">Figure 7
<p>The output of the ProVerif to check session key secrecy, patient’s anonimity and resistance against replay, impersonation and message modification attacks.</p> Full article ">Figure 8
<p>The output of the ProVerif execution to check the PFS property.</p> Full article ">
<p>Overview of the remote health care system.</p> Full article ">Figure 2
<p>Registration of a physician at the gateway.</p> Full article ">Figure 3
<p>Registration of a patient at the supervisor.</p> Full article ">Figure 4
<p>Registration of a supervisor at the gateway.</p> Full article ">Figure 5
<p>General architecture of the proposed authenticated key agreement scheme including main steps.</p> Full article ">Figure 6
<p>Authentication and session key generation.</p> Full article ">Figure 7
<p>The output of the ProVerif to check session key secrecy, patient’s anonimity and resistance against replay, impersonation and message modification attacks.</p> Full article ">Figure 8
<p>The output of the ProVerif execution to check the PFS property.</p> Full article ">
Open AccessFeature PaperArticle
A Secure Approach Out-of-Band for e-Bank with Visual Two-Factor Authorization Protocol
by
Laerte Peotta de Melo, Dino Macedo Amaral, Robson de Oliveira Albuquerque, Rafael Timóteo de Sousa Júnior, Ana Lucila Sandoval Orozco and Luis Javier García Villalba
Cryptography 2024, 8(4), 51; https://doi.org/10.3390/cryptography8040051 - 11 Nov 2024
Abstract
►▼
Show Figures
The article presents an innovative approach for secure authentication in internet banking transactions, utilizing an Out-of-Band visual two-factor authorization protocol. With the increasing rise of cyber attacks and fraud, new security models are needed that ensure the integrity, authenticity, and confidentiality of financial
[...] Read more.
The article presents an innovative approach for secure authentication in internet banking transactions, utilizing an Out-of-Band visual two-factor authorization protocol. With the increasing rise of cyber attacks and fraud, new security models are needed that ensure the integrity, authenticity, and confidentiality of financial transactions. The identified gap lies in the inability of traditional authentication methods, such as TANs and tokens, to provide security in untrusted terminals. The proposed solution is the Dynamic Authorization Protocol (DAP), which uses mobile devices to validate transactions through visual codes, such as QR codes. Each transaction is assigned a unique associated code, and the challenge must be responded to within 120 s. The customer initiates the transaction on a computer and independently validates it on their mobile device using an out-of-band channel to prevent attacks such as phishing and man-in-the-middle. The methodology involves implementing a prototype in Java ME for Android devices and a Java application server, creating a practical, low-computational-cost system, accessible for use across different operating systems and devices. The protocol was tested in real-world scenarios, focusing on ensuring transaction integrity and authenticity. The results show a successful implementation at Banco do Brasil, with 3.6 million active users, demonstrating the efficiency of the model over 12 years of use without significant vulnerabilities. The DAP protocol provides a robust and effective solution for securing banking transactions and can be extended to other authentication environments, such as payment terminals and point of sale devices.
Full article
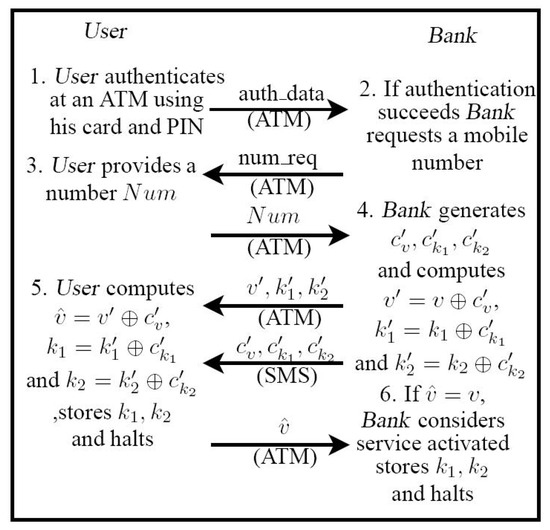
Figure 1
Figure 1
<p>Key Change.</p> Full article ">Figure 2
<p>Authentication Messages.</p> Full article ">Figure 3
<p>Generation of seeds Master Key.</p> Full article ">Figure 4
<p>Key Exchange—<math display="inline"><semantics> <msub> <mi>k</mi> <mn>1</mn> </msub> </semantics></math>.</p> Full article ">Figure 5
<p>Key Exchange—<math display="inline"><semantics> <msub> <mi>k</mi> <mn>2</mn> </msub> </semantics></math>.</p> Full article ">Figure 6
<p>Asymmetric cryptographic keys Model.</p> Full article ">Figure 7
<p>Transaction authorization flow.</p> Full article ">Figure 8
<p>Challenge response displayed on the untrusted computer.</p> Full article ">Figure 9
<p>Cellphone transaction check.</p> Full article ">Figure 10
<p>Cellphone authorization code view.</p> Full article ">Figure 11
<p>Diagram Personification of Customer Attack.</p> Full article ">Figure 12
<p>Diagram Control Device Attack.</p> Full article ">Figure 13
<p>Number of Users.</p> Full article ">
<p>Key Change.</p> Full article ">Figure 2
<p>Authentication Messages.</p> Full article ">Figure 3
<p>Generation of seeds Master Key.</p> Full article ">Figure 4
<p>Key Exchange—<math display="inline"><semantics> <msub> <mi>k</mi> <mn>1</mn> </msub> </semantics></math>.</p> Full article ">Figure 5
<p>Key Exchange—<math display="inline"><semantics> <msub> <mi>k</mi> <mn>2</mn> </msub> </semantics></math>.</p> Full article ">Figure 6
<p>Asymmetric cryptographic keys Model.</p> Full article ">Figure 7
<p>Transaction authorization flow.</p> Full article ">Figure 8
<p>Challenge response displayed on the untrusted computer.</p> Full article ">Figure 9
<p>Cellphone transaction check.</p> Full article ">Figure 10
<p>Cellphone authorization code view.</p> Full article ">Figure 11
<p>Diagram Personification of Customer Attack.</p> Full article ">Figure 12
<p>Diagram Control Device Attack.</p> Full article ">Figure 13
<p>Number of Users.</p> Full article ">
Open AccessFeature PaperArticle
Quantum Security of a Compact Multi-Signature
by
Shaoquan Jiang
Cryptography 2024, 8(4), 50; https://doi.org/10.3390/cryptography8040050 - 28 Oct 2024
Abstract
►▼
Show Figures
With the rapid advances in quantum computing, quantum security is now an indispensable property for any cryptographic system. In this paper, we study how to prove the security of a complex cryptographic system in the quantum random oracle model. We first give a
[...] Read more.
With the rapid advances in quantum computing, quantum security is now an indispensable property for any cryptographic system. In this paper, we study how to prove the security of a complex cryptographic system in the quantum random oracle model. We first give a variant of Zhandry’s compressed random oracle (CStO), called a compressed quantum random oracle with adaptive special points (CStOs). Then, we extend the on-line extraction technique of Don et al. (EUROCRYPT’22) from CStO to
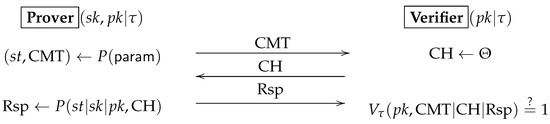
Figure 1
Open AccessArticle
Design and Performance Evaluation of an Authentic End-to-End Communication Model on Large-Scale Hybrid IPv4-IPv6 Virtual Networks to Detect MITM Attacks
by
Zeeshan Ashraf, Adnan Sohail and Muddesar Iqbal
Cryptography 2024, 8(4), 49; https://doi.org/10.3390/cryptography8040049 - 28 Oct 2024
Abstract
►▼
Show Figures
After the end of IPv4 addresses, the Internet is moving towards IPv6 address architecture quickly with the support of virtualization techniques worldwide. IPv4 and IPv6 protocols will co-exist long during the changeover process. Some attacks, such as MITM attacks, do not discriminate by
[...] Read more.
After the end of IPv4 addresses, the Internet is moving towards IPv6 address architecture quickly with the support of virtualization techniques worldwide. IPv4 and IPv6 protocols will co-exist long during the changeover process. Some attacks, such as MITM attacks, do not discriminate by appearance and affect IPv4 and IPv6 address architectures. In an MITM attack, the attacker secretly captures the data, masquerades as the original sender, and sends it toward the receiver. The receiver replies to the attacker because the receiver does not authenticate the source. Therefore, the authentication between two parties is compromised due to an MITM attack. The existing authentication schemes adopt complicated mathematical procedures. Therefore, the existing schemes increase computation and communication costs. This paper proposes a lightweight and authentic end-to-end communication model to detect MITM attacks using a pre-shared symmetric key. In addition, we implement and analyze the performance of our proposed security model on Linux-based virtual machines connected to large-scale hybrid IPv4-IPv6 virtual networks. Moreover, security analyses prove the effectiveness of our proposed model. Finally, we compare the performance of our proposed security model with existing models in terms of computation cost and communication overhead.
Full article
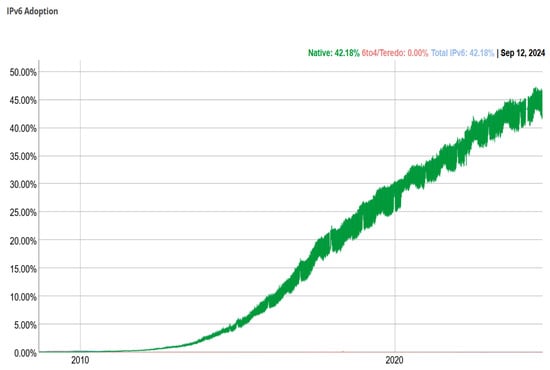
Figure 1
Figure 1
<p>IPv6 adoption.</p> Full article ">Figure 2
<p>MITM attack.</p> Full article ">Figure 3
<p>Authentic client–server communication model.</p> Full article ">Figure 4
<p>Key exchange and authentication process.</p> Full article ">Figure 5
<p>MITM attack detection.</p> Full article ">Figure 6
<p>Results through AVISPA.</p> Full article ">Figure 7
<p>Hybrid IPv4-IPv6 Experimental Setup.</p> Full article ">Figure 8
<p>Output on server.</p> Full article ">Figure 9
<p>Output on client.</p> Full article ">Figure 10
<p>Convergence time over hybrid IPv4-IPv6 networks.</p> Full article ">Figure 11
<p>RTT for IPv4-IPv6 networks.</p> Full article ">Figure 12
<p>Throughput for IPv4-IPv6 networks.</p> Full article ">Figure 13
<p>Jitter for IPv4-IPv6 Networks.</p> Full article ">Figure 14
<p>Packet loss ratio for IPv4-IPv6 networks.</p> Full article ">
<p>IPv6 adoption.</p> Full article ">Figure 2
<p>MITM attack.</p> Full article ">Figure 3
<p>Authentic client–server communication model.</p> Full article ">Figure 4
<p>Key exchange and authentication process.</p> Full article ">Figure 5
<p>MITM attack detection.</p> Full article ">Figure 6
<p>Results through AVISPA.</p> Full article ">Figure 7
<p>Hybrid IPv4-IPv6 Experimental Setup.</p> Full article ">Figure 8
<p>Output on server.</p> Full article ">Figure 9
<p>Output on client.</p> Full article ">Figure 10
<p>Convergence time over hybrid IPv4-IPv6 networks.</p> Full article ">Figure 11
<p>RTT for IPv4-IPv6 networks.</p> Full article ">Figure 12
<p>Throughput for IPv4-IPv6 networks.</p> Full article ">Figure 13
<p>Jitter for IPv4-IPv6 Networks.</p> Full article ">Figure 14
<p>Packet loss ratio for IPv4-IPv6 networks.</p> Full article ">
Open AccessArticle
Post-Quantum Secure ID-Based (Threshold) Linkable Dual-Ring Signature and Its Application in Blockchain Transactions
by
Wen Gao, Haoyuan Yao, Baodong Qin, Xiaoli Dong, Zhen Zhao and Jiayu Zeng
Cryptography 2024, 8(4), 48; https://doi.org/10.3390/cryptography8040048 - 28 Oct 2024
Abstract
►▼
Show Figures
Ring signatures are widely used in e-voting, anonymous whistle-blowing systems, and blockchain transactions. However, due to the anonymity of ring signatures, a signer can sign the same message multiple times, potentially leading to repeated voting or double spending in blockchain transactions. To address
[...] Read more.
Ring signatures are widely used in e-voting, anonymous whistle-blowing systems, and blockchain transactions. However, due to the anonymity of ring signatures, a signer can sign the same message multiple times, potentially leading to repeated voting or double spending in blockchain transactions. To address these issues in blockchain transactions, this work constructs an identity-based linkable ring signature scheme based on the hardness of the lattice-based Module Small Integer Solution (M-SIS) assumption, which is hard even for quantum attackers. The proposed scheme is proven to be anonymous, unforgeable, linkable, and nonslanderable in the random oracle model. Compared to existing identity-based linkable ring signature (IBLRS) schemes of linear size, our signature size is relatively smaller, and this advantage is more pronounced when the number of ring members is small. We provide approximate signature size data for ring members ranging from 2 to 2048. When the number of ring members is 16 (or 512. resp.), the signature size of our scheme is 11.40 KB (or 24.68 KB, respectively). Finally, a threshold extension is given as an additional scheme with specifications and security analysis.
Full article
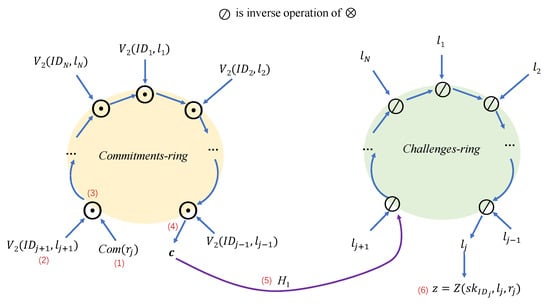
Figure 1
Figure 1
<p>Structure of dual-ring structure.</p> Full article ">Figure 2
<p>Definition of identity-based linkable ring signature.</p> Full article ">Figure 3
<p>System model of IB-LDRS in blockchain transactions.</p> Full article ">Figure 4
<p>Communication costs with numbers of ring members.</p> Full article ">
<p>Structure of dual-ring structure.</p> Full article ">Figure 2
<p>Definition of identity-based linkable ring signature.</p> Full article ">Figure 3
<p>System model of IB-LDRS in blockchain transactions.</p> Full article ">Figure 4
<p>Communication costs with numbers of ring members.</p> Full article ">
Open AccessArticle
Next-Generation Block Ciphers: Achieving Superior Memory Efficiency and Cryptographic Robustness for IoT Devices
by
Saadia Aziz, Ijaz Ali Shoukat, Mohsin Iftikhar, Mohsin Murtaza, Abdulmajeed M. Alenezi, Cheng-Chi Lee and Imran Taj
Cryptography 2024, 8(4), 47; https://doi.org/10.3390/cryptography8040047 - 23 Oct 2024
Abstract
Traditional cryptographic methods often need complex designs that require substantial memory and battery power, rendering them unsuitable for small handheld devices. As the prevalence of these devices continues to rise, there is a pressing need to develop smart, memory-efficient cryptographic protocols that provide
[...] Read more.
Traditional cryptographic methods often need complex designs that require substantial memory and battery power, rendering them unsuitable for small handheld devices. As the prevalence of these devices continues to rise, there is a pressing need to develop smart, memory-efficient cryptographic protocols that provide both high speed and robust security. Current solutions, primarily dependent on dynamic permutations, fall short in terms of encryption and decryption speeds, the cryptographic strength, and the memory efficiency. Consequently, the evolution of lightweight cryptographic algorithms incorporating randomised substitution properties is imperative to meet the stringent security demands of handheld devices effectively. In this paper, we present an advanced design of lightweight block ciphers that enhances traditional dynamic permutations with innovative randomised substitutions. This design utilises straightforward randomized encryption methods such as XOR, nibble swap, count ones, and left shift. The cryptographic robustness of our proposed block cipher has been rigorously tested through several standardised statistical tests, as recommended by the National Institute of Standards and Technology (NIST). These evaluations confirm that our algorithm maintains strong cryptographic properties with randomised substitutions and outperforms existing models in several key aspects. Moreover, comparative assessments reveal that our algorithm achieves a throughput of 853.31 Kbps while consuming only 1510 bytes of memory and demonstrating over 60% avalanche properties, significantly outperforming other solutions in terms of CPU utilisation and memory consumption. These results underscore the efficacy of our approach in fulfilling the advanced security requirements of modern handheld devices.
Full article
(This article belongs to the Special Issue Advances in Authentication, Authorization and Privacy for Securing Smart Communications)
►▼
Show Figures
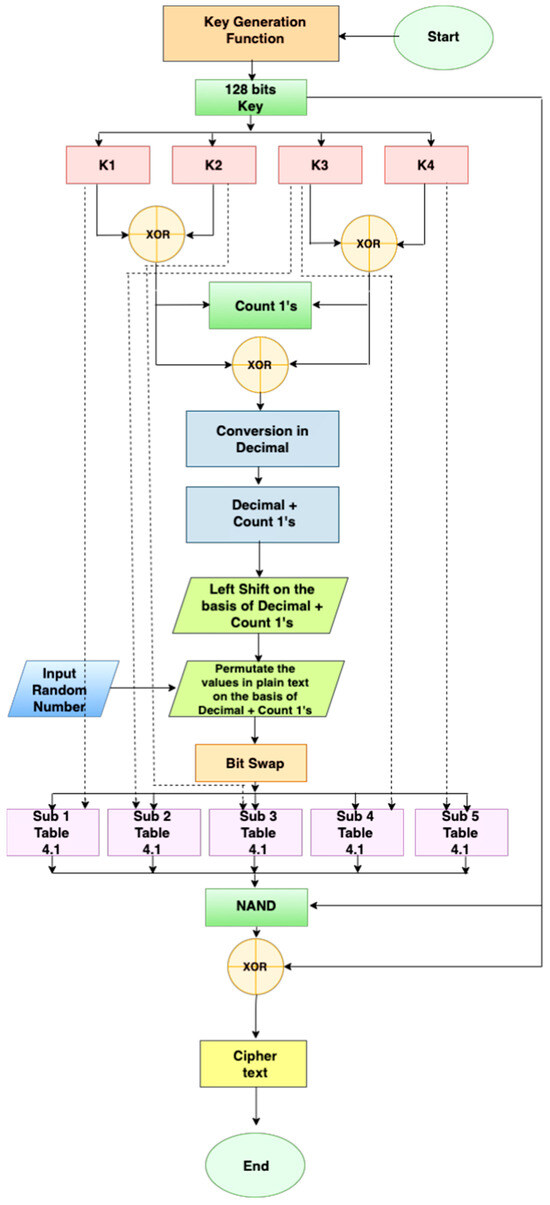
Figure 1
Figure 1
<p>Working scheme of the proposed method.</p> Full article ">Figure 2
<p>Working scheme of key generation of proposed method.</p> Full article ">Figure 3
<p>Comparison of brute force attack with existing algorithms.</p> Full article ">Figure 4
<p>Comparison of the average avalanche for the plaintext [<a href="#B10-cryptography-08-00047" class="html-bibr">10</a>,<a href="#B15-cryptography-08-00047" class="html-bibr">15</a>,<a href="#B67-cryptography-08-00047" class="html-bibr">67</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B69-cryptography-08-00047" class="html-bibr">69</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 5
<p>Comparison of the average avalanche effect for the key [<a href="#B10-cryptography-08-00047" class="html-bibr">10</a>,<a href="#B11-cryptography-08-00047" class="html-bibr">11</a>,<a href="#B15-cryptography-08-00047" class="html-bibr">15</a>,<a href="#B67-cryptography-08-00047" class="html-bibr">67</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B69-cryptography-08-00047" class="html-bibr">69</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 6
<p>Memory comparison with proposed algorithm.</p> Full article ">Figure 7
<p>Throughput comparison with proposed algorithm [<a href="#B3-cryptography-08-00047" class="html-bibr">3</a>,<a href="#B4-cryptography-08-00047" class="html-bibr">4</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 8
<p>Statistical test for randomness.</p> Full article ">
<p>Working scheme of the proposed method.</p> Full article ">Figure 2
<p>Working scheme of key generation of proposed method.</p> Full article ">Figure 3
<p>Comparison of brute force attack with existing algorithms.</p> Full article ">Figure 4
<p>Comparison of the average avalanche for the plaintext [<a href="#B10-cryptography-08-00047" class="html-bibr">10</a>,<a href="#B15-cryptography-08-00047" class="html-bibr">15</a>,<a href="#B67-cryptography-08-00047" class="html-bibr">67</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B69-cryptography-08-00047" class="html-bibr">69</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 5
<p>Comparison of the average avalanche effect for the key [<a href="#B10-cryptography-08-00047" class="html-bibr">10</a>,<a href="#B11-cryptography-08-00047" class="html-bibr">11</a>,<a href="#B15-cryptography-08-00047" class="html-bibr">15</a>,<a href="#B67-cryptography-08-00047" class="html-bibr">67</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B69-cryptography-08-00047" class="html-bibr">69</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 6
<p>Memory comparison with proposed algorithm.</p> Full article ">Figure 7
<p>Throughput comparison with proposed algorithm [<a href="#B3-cryptography-08-00047" class="html-bibr">3</a>,<a href="#B4-cryptography-08-00047" class="html-bibr">4</a>,<a href="#B68-cryptography-08-00047" class="html-bibr">68</a>,<a href="#B70-cryptography-08-00047" class="html-bibr">70</a>].</p> Full article ">Figure 8
<p>Statistical test for randomness.</p> Full article ">
Open AccessArticle
Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions
by
Cyrus Minwalla, Jim Plusquellic and Eirini Eleni Tsiropoulou
Cryptography 2024, 8(4), 46; https://doi.org/10.3390/cryptography8040046 - 19 Oct 2024
Abstract
Authenticated key exchange is desired in scenarios where two participants must exchange sensitive information over an untrusted channel but do not trust each other at the outset of the exchange. As a unique hardware-based random oracle, physical unclonable functions (PUFs) can embed cryptographic
[...] Read more.
Authenticated key exchange is desired in scenarios where two participants must exchange sensitive information over an untrusted channel but do not trust each other at the outset of the exchange. As a unique hardware-based random oracle, physical unclonable functions (PUFs) can embed cryptographic hardness and binding properties needed for a secure, interactive authentication system. In this paper, we propose a lightweight protocol, termed PUF-MAKE, to achieve bilateral mutual authentication between two untrusted parties with the help of a trusted server and secure physical devices. At the end of the protocol, both parties are authenticated and possess a shared session key that they can use to encrypt sensitive information over an untrusted channel. The PUF’s underlying entropy hardness characteristics and the key-encryption-key (KEK) primitive act as the root of trust in the protocol’s construction. Other salient properties include a lightweight construction with minimal information stored on each device, a key refresh mechanism to ensure a fresh key is used for every authentication, and robustness against a wide range of attacks. We evaluate the protocol on a set of three FPGAs and a desktop server, with the computational complexity calculated as a function of primitive operations. A composable security model is proposed and analyzed considering a powerful adversary in control of all communications channels. In particular, session key confidentiality is proven through formal verification of the protocol under strong attacker (Dolev-Yao) assumptions, rendering it viable for high-security applications such as digital currency.
Full article
(This article belongs to the Section Hardware Security)
►▼
Show Figures
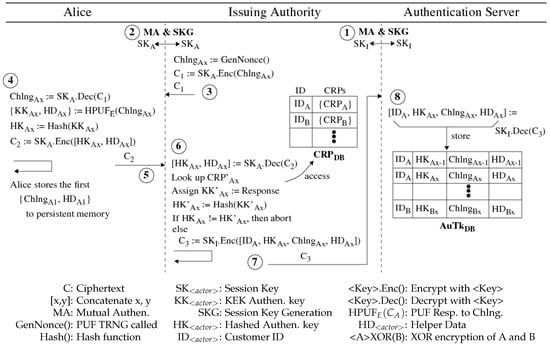
Figure 1
Figure 1
<p>Message exchange diagram for PUF-MAKE Enrollment.</p> Full article ">Figure 2
<p>Message exchange diagram for in-field authentication between Alice and Bob. The strike-outs, indicated with red lines in the <math display="inline"><semantics> <mrow> <mi>A</mi> <mi>u</mi> <mi>T</mi> <msub> <mi>k</mi> <mrow> <mi>D</mi> <mi>B</mi> </mrow> </msub> </mrow> </semantics></math>, identify used AT that are deleted from the database.</p> Full article ">Figure 3
<p>A formally verified model of in-field authentication.</p> Full article ">Figure 4
<p>Established queries for formal verification.</p> Full article ">Figure 5
<p>Entropy and MinEntropy of 10,000 <math display="inline"><semantics> <msub> <mi>KK</mi> <mi>A</mi> </msub> </semantics></math> that are generated over a 4.5 h run of the MAKE protocol.</p> Full article ">Figure 6
<p>Intra-chip Hamming Distance statistics for 10,000 KK from Alice and Bob’s devices (superimposed curves), produced in one minute time intervals over a 4.5 h duration.</p> Full article ">Figure 7
<p>Transaction times of PUF-MAKE In-Field protocol steps: (1) <math display="inline"><semantics> <msub> <mi>SK</mi> <mi>T</mi> </msub> </semantics></math> generation; (2) <math display="inline"><semantics> <msub> <mi>KK</mi> <mi>A</mi> </msub> </semantics></math> generation and hash to <math display="inline"><semantics> <msub> <mi>HK</mi> <mi>A</mi> </msub> </semantics></math>; (3) <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mn>1</mn> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mn>2</mn> </msub> </semantics></math> creation and transmission to AS; (4) DB search, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>A</mi> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>B</mi> </msub> </semantics></math> creation and transmission from AS; (5) <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>A</mi> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>B</mi> </msub> </semantics></math> extraction and SK creation; (6) Encrypt-transmit-decrypt test message with SK; and (7) total authentication time.</p> Full article ">
<p>Message exchange diagram for PUF-MAKE Enrollment.</p> Full article ">Figure 2
<p>Message exchange diagram for in-field authentication between Alice and Bob. The strike-outs, indicated with red lines in the <math display="inline"><semantics> <mrow> <mi>A</mi> <mi>u</mi> <mi>T</mi> <msub> <mi>k</mi> <mrow> <mi>D</mi> <mi>B</mi> </mrow> </msub> </mrow> </semantics></math>, identify used AT that are deleted from the database.</p> Full article ">Figure 3
<p>A formally verified model of in-field authentication.</p> Full article ">Figure 4
<p>Established queries for formal verification.</p> Full article ">Figure 5
<p>Entropy and MinEntropy of 10,000 <math display="inline"><semantics> <msub> <mi>KK</mi> <mi>A</mi> </msub> </semantics></math> that are generated over a 4.5 h run of the MAKE protocol.</p> Full article ">Figure 6
<p>Intra-chip Hamming Distance statistics for 10,000 KK from Alice and Bob’s devices (superimposed curves), produced in one minute time intervals over a 4.5 h duration.</p> Full article ">Figure 7
<p>Transaction times of PUF-MAKE In-Field protocol steps: (1) <math display="inline"><semantics> <msub> <mi>SK</mi> <mi>T</mi> </msub> </semantics></math> generation; (2) <math display="inline"><semantics> <msub> <mi>KK</mi> <mi>A</mi> </msub> </semantics></math> generation and hash to <math display="inline"><semantics> <msub> <mi>HK</mi> <mi>A</mi> </msub> </semantics></math>; (3) <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mn>1</mn> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mn>2</mn> </msub> </semantics></math> creation and transmission to AS; (4) DB search, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>A</mi> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>B</mi> </msub> </semantics></math> creation and transmission from AS; (5) <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>A</mi> </msub> </semantics></math>, <math display="inline"><semantics> <msub> <mi mathvariant="normal">C</mi> <mi>B</mi> </msub> </semantics></math> extraction and SK creation; (6) Encrypt-transmit-decrypt test message with SK; and (7) total authentication time.</p> Full article ">
Open AccessArticle
Combined and General Methodologies of Key Space Partition for the Cryptanalysis of Block Ciphers
by
Mijail Borges-Quintana, Miguel A. Borges-Trenard, Osmani Tito-Corrioso, Omar Rojas and Guillermo Sosa-Gómez
Cryptography 2024, 8(4), 45; https://doi.org/10.3390/cryptography8040045 - 11 Oct 2024
Abstract
This paper proposes two new methods of key space partitioning for the cryptanalysis of block ciphers. The first one is called combined methodology of key space partition (CoMeKSPar), which allows us to simultaneously set some of the first and last consecutive bits of
[...] Read more.
This paper proposes two new methods of key space partitioning for the cryptanalysis of block ciphers. The first one is called combined methodology of key space partition (CoMeKSPar), which allows us to simultaneously set some of the first and last consecutive bits of the key. In this way, the search is performed using the remaining middle bits. CoMeKSPar is a combination of two methods already proposed in the scientific literature, the Borges, Borges, Monier (BBM) and the Tito, Borges, Borges (TBB). The second method is called the general algorithm of key space reduction (GAKSRed), which makes it possible to perform a genetic algorithm search in the space formed by the unknown bits of the key, regardless of their distribution in the binary block. Furthermore, a method of attacking block ciphers is presented for the case where some key bits are known; the basic idea is to deduce some of the remaining bits of the block. An advantage of these methods is that they allow parallel computing, which allows simultaneous searches in different sub-blocks of key bits, thereby increasing the probability of success. The experiments are performed with the KLEIN (Small) lightweight block cipher using the genetic algorithm.
Full article
(This article belongs to the Topic Recent Advances in Security, Privacy, and Trust)
Open AccessArticle
Partial Exposure Attacks on a New RSA Variant
by
Mohammed Rahmani, Abderrahmane Nitaj and Mhammed Ziane
Cryptography 2024, 8(4), 44; https://doi.org/10.3390/cryptography8040044 - 6 Oct 2024
Abstract
In 2022, Cotan and Teşeleanu presented a variant of the RSA cryptosystem where the modulus is of the form
In 2022, Cotan and Teşeleanu presented a variant of the RSA cryptosystem where the modulus is of the form
Open AccessArticle
CHAM-CLAS: A Certificateless Aggregate Signature Scheme with Chameleon Hashing-Based Identity Authentication for VANETs
by
Ahmad Kabil, Heba Aslan, Marianne A. Azer and Mohamed Rasslan
Cryptography 2024, 8(3), 43; https://doi.org/10.3390/cryptography8030043 - 17 Sep 2024
Abstract
►▼
Show Figures
Vehicular ad hoc networks (VANETs), which are the backbone of intelligent transportation systems (ITSs), facilitate critical data exchanges between vehicles. This necessitates secure transmission, which requires guarantees of message availability, integrity, source authenticity, and user privacy. Moreover, the traceability of network participants is
[...] Read more.
Vehicular ad hoc networks (VANETs), which are the backbone of intelligent transportation systems (ITSs), facilitate critical data exchanges between vehicles. This necessitates secure transmission, which requires guarantees of message availability, integrity, source authenticity, and user privacy. Moreover, the traceability of network participants is essential as it deters malicious actors and allows lawful authorities to identify message senders for accountability. This introduces a challenge: balancing privacy with traceability. Conditional privacy-preserving authentication (CPPA) schemes are designed to mitigate this conflict. CPPA schemes utilize cryptographic protocols, including certificate-based schemes, group signatures, identity-based schemes, and certificateless schemes. Due to the critical time constraints in VANETs, efficient batch verification techniques are crucial. Combining certificateless schemes with batch verification leads to certificateless aggregate signature (CLAS) schemes. In this paper, cryptanalysis of Xiong’s CLAS scheme revealed its vulnerabilities to partial key replacement and identity replacement attacks, alongside mathematical errors in the batch verification process. Our proposed CLAS scheme remedies these issues by incorporating an identity authentication module that leverages chameleon hashing within elliptic curve cryptography (CHAM-CLAS). The signature and verification modules are also redesigned to address the identified vulnerabilities in Xiong’s scheme. Additionally, we implemented the small exponents test within the batch verification module to achieve Type III security. While this enhances security, it introduces a slight performance trade-off. Our scheme has been subjected to formal security and performance analyses to ensure robustness.
Full article
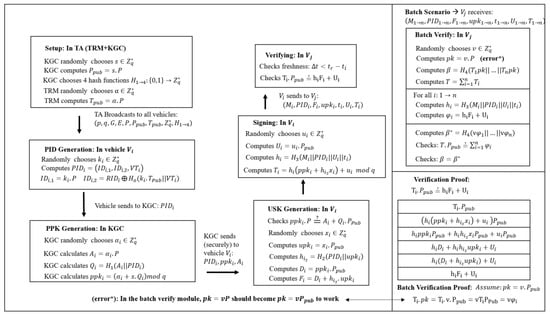
Figure 1
Figure 1
<p>Visual diagram of Xiong’s scheme.</p> Full article ">Figure 2
<p>Attacks on Xiong’s scheme.</p> Full article ">Figure 3
<p>(<b>A</b>) Visual diagram of our CHAM-HASH-based CLAS scheme; (<b>B</b>) Batch verification component of our CLAS scheme and proof of correctness.</p> Full article ">Figure 4
<p>Batch verification time (in milliseconds) for different values of n (number of signatures).</p> Full article ">
<p>Visual diagram of Xiong’s scheme.</p> Full article ">Figure 2
<p>Attacks on Xiong’s scheme.</p> Full article ">Figure 3
<p>(<b>A</b>) Visual diagram of our CHAM-HASH-based CLAS scheme; (<b>B</b>) Batch verification component of our CLAS scheme and proof of correctness.</p> Full article ">Figure 4
<p>Batch verification time (in milliseconds) for different values of n (number of signatures).</p> Full article ">
Open AccessArticle
A Multi-Candidate Self-Tallying Voting Scheme Based on Smart Contracts
by
Xingan Dai, Xinquan Zhou, Dehua Zhou, Jinhan Zhong and Chao Hong
Cryptography 2024, 8(3), 42; https://doi.org/10.3390/cryptography8030042 - 12 Sep 2024
Abstract
In this paper, we propose a smart contract-based multi-candidate self-tallying voting scheme in order to guarantee the privacy of ballots in the case of multiple candidates. This scheme uses the ElGamal cryptosystem to ensure the security of the ballots, and combines it with
[...] Read more.
In this paper, we propose a smart contract-based multi-candidate self-tallying voting scheme in order to guarantee the privacy of ballots in the case of multiple candidates. This scheme uses the ElGamal cryptosystem to ensure the security of the ballots, and combines it with a Distributed Encryption algorithm to make the voting scheme have self-tallying features, and guarantees the correctness of the intermediate data through zero-knowledge proofs. The experimental results show that the scheme improves the voting efficiency without compromising the security.
Full article
(This article belongs to the Section Blockchain Security)
►▼
Show Figures
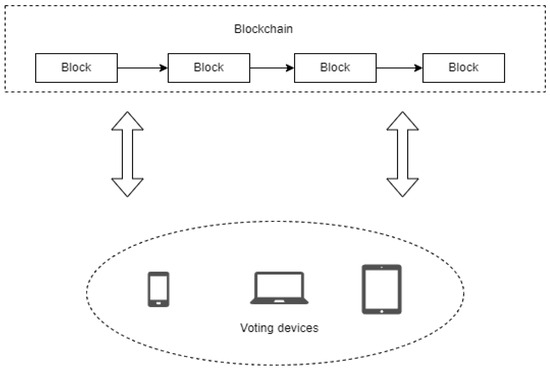
Figure 1
Figure 1
<p>Framework for the self-tallying voting schemes.</p> Full article ">Figure 2
<p>Workflow of the decentralized self-tallying scheme.</p> Full article ">Figure 3
<p>The generation process of <math display="inline"><semantics> <mrow> <mi>Z</mi> <mi>K</mi> <mi>P</mi> <mo>(</mo> <msub> <mi>C</mi> <mrow> <mi>i</mi> <mo>,</mo> <mi>j</mi> </mrow> </msub> <mo>)</mo> </mrow> </semantics></math>.</p> Full article ">Figure 4
<p>Encryption Time on voting.</p> Full article ">Figure 5
<p>Time used for encrypting ballots, counting votes and zero-knowledge proofs.</p> Full article ">Figure 6
<p>Time spent on the validation process.</p> Full article ">
<p>Framework for the self-tallying voting schemes.</p> Full article ">Figure 2
<p>Workflow of the decentralized self-tallying scheme.</p> Full article ">Figure 3
<p>The generation process of <math display="inline"><semantics> <mrow> <mi>Z</mi> <mi>K</mi> <mi>P</mi> <mo>(</mo> <msub> <mi>C</mi> <mrow> <mi>i</mi> <mo>,</mo> <mi>j</mi> </mrow> </msub> <mo>)</mo> </mrow> </semantics></math>.</p> Full article ">Figure 4
<p>Encryption Time on voting.</p> Full article ">Figure 5
<p>Time used for encrypting ballots, counting votes and zero-knowledge proofs.</p> Full article ">Figure 6
<p>Time spent on the validation process.</p> Full article ">
Open AccessArticle
Cryptanalysis of Dual-Stage Permutation Encryption Using Large-Kernel Convolutional Neural Network and Known Plaintext Attack
by
Ching-Chun Chang, Shuying Xu, Kai Gao and Chin-Chen Chang
Cryptography 2024, 8(3), 41; https://doi.org/10.3390/cryptography8030041 - 11 Sep 2024
Abstract
Reversible data-hiding in encrypted images (RDHEI) plays a pivotal role in preserving privacy within images stored on cloud platforms. Recently, Wang et al. introduced a dual-stage permutation encryption scheme, which is highly compatible with RDHEI techniques. In this study, we undertake an exhaustive
[...] Read more.
Reversible data-hiding in encrypted images (RDHEI) plays a pivotal role in preserving privacy within images stored on cloud platforms. Recently, Wang et al. introduced a dual-stage permutation encryption scheme, which is highly compatible with RDHEI techniques. In this study, we undertake an exhaustive examination of the characteristics inherent to the dual-stage permutation scheme and propose two cryptanalysis schemes leveraging a large-kernel convolutional neural network (LKCNN) and a known plaintext attack (KPA) scheme, respectively. Our experimental findings demonstrate the effectiveness of our cryptanalysis schemes in breaking the dual-stage permutation encryption scheme. Based on our investigation, we highlight significant security vulnerabilities in the dual-stage permutation encryption scheme, raising concerns about its suitability for secure image storage and privacy protection in cloud environments.
Full article
(This article belongs to the Special Issue Advances in Authentication, Authorization and Privacy for Securing Smart Communications)
►▼
Show Figures
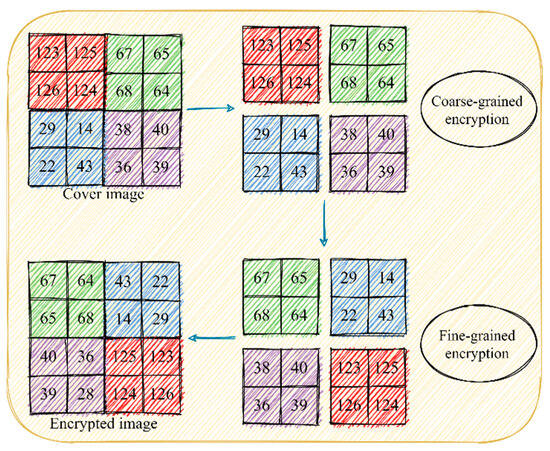
Figure 1
Figure 1
<p>Schematic diagram of image encryption, where different colors represent different blocks.</p> Full article ">Figure 2
<p>Network architecture of LKCNN. (<b>a</b>) The network architecture. (<b>b</b>) The network layer indication.</p> Full article ">Figure 3
<p>Four <math display="inline"><semantics> <mrow> <mn>256</mn> <mo>×</mo> <mn>256</mn> </mrow> </semantics></math>-sized test images. (<b>a1</b>–<b>a4</b>) are test images, (<b>b1</b>–<b>b4</b>) are the corresponding ciphertext images.</p> Full article ">Figure 4
<p>The accuracy of <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math> obtained by “Baboon”, “Airplane”, and “Peppers” under 100 different encryption keys. (<b>a</b>–<b>c</b>) are accuracy results of “Baboon”, “Airplane”, and “Peppers”, respectively.</p> Full article ">Figure 4 Cont.
<p>The accuracy of <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math> obtained by “Baboon”, “Airplane”, and “Peppers” under 100 different encryption keys. (<b>a</b>–<b>c</b>) are accuracy results of “Baboon”, “Airplane”, and “Peppers”, respectively.</p> Full article ">Figure 5
<p>The decrypted ciphertext of “Barbara” using the known plaintext image of “Baboon”, “Peppers”, and “Airplane”.</p> Full article ">Figure 6
<p>The influence of the number of known plaintext images on the estimation accuracy of the estimated sequences <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math>.</p> Full article ">Figure 7
<p>Samples of dataset.</p> Full article ">Figure 8
<p>Misclassified samples.</p> Full article ">Figure 8 Cont.
<p>Misclassified samples.</p> Full article ">Figure 9
<p>Four reconstructed images.</p> Full article ">
<p>Schematic diagram of image encryption, where different colors represent different blocks.</p> Full article ">Figure 2
<p>Network architecture of LKCNN. (<b>a</b>) The network architecture. (<b>b</b>) The network layer indication.</p> Full article ">Figure 3
<p>Four <math display="inline"><semantics> <mrow> <mn>256</mn> <mo>×</mo> <mn>256</mn> </mrow> </semantics></math>-sized test images. (<b>a1</b>–<b>a4</b>) are test images, (<b>b1</b>–<b>b4</b>) are the corresponding ciphertext images.</p> Full article ">Figure 4
<p>The accuracy of <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math> obtained by “Baboon”, “Airplane”, and “Peppers” under 100 different encryption keys. (<b>a</b>–<b>c</b>) are accuracy results of “Baboon”, “Airplane”, and “Peppers”, respectively.</p> Full article ">Figure 4 Cont.
<p>The accuracy of <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math> obtained by “Baboon”, “Airplane”, and “Peppers” under 100 different encryption keys. (<b>a</b>–<b>c</b>) are accuracy results of “Baboon”, “Airplane”, and “Peppers”, respectively.</p> Full article ">Figure 5
<p>The decrypted ciphertext of “Barbara” using the known plaintext image of “Baboon”, “Peppers”, and “Airplane”.</p> Full article ">Figure 6
<p>The influence of the number of known plaintext images on the estimation accuracy of the estimated sequences <math display="inline"><semantics> <mrow> <mstyle displaystyle="true"> <mover accent="true"> <mrow> <mo>∏</mo> </mrow> <mo stretchy="true">^</mo> </mover> </mstyle> </mrow> </semantics></math> and <math display="inline"><semantics> <mrow> <mover accent="true"> <mrow> <mi mathvariant="sans-serif">Φ</mi> </mrow> <mo>^</mo> </mover> </mrow> </semantics></math>.</p> Full article ">Figure 7
<p>Samples of dataset.</p> Full article ">Figure 8
<p>Misclassified samples.</p> Full article ">Figure 8 Cont.
<p>Misclassified samples.</p> Full article ">Figure 9
<p>Four reconstructed images.</p> Full article ">
Open AccessArticle
Strict Avalanche Criterion of SHA-256 and Sub-Function-Removed Variants
by
Riley Vaughn and Mike Borowczak
Cryptography 2024, 8(3), 40; https://doi.org/10.3390/cryptography8030040 - 8 Sep 2024
Abstract
►▼
Show Figures
The measure of diffusion, the property of dissipating patterns and statistical structures in cryptographic transformations, serves as a valuable heuristic for assessing the obscurity of patterns that could lead to collisions. As with many cryptographic hash functions, SHA-256 is thought to exhibit the
[...] Read more.
The measure of diffusion, the property of dissipating patterns and statistical structures in cryptographic transformations, serves as a valuable heuristic for assessing the obscurity of patterns that could lead to collisions. As with many cryptographic hash functions, SHA-256 is thought to exhibit the property of diffusion. While SHA-256’s diffuse output is loosely documented, even less is known about how the diffusion rate changes across the 64 rounds in its compression function and how the algorithm’s individual sub-functions contribute to the overall diffusion. The diffusion of the unmodified compression function is initially measured using the Strict Avalanche Criterion (SAC), with the aim of understanding the alteration in diffusion across the 64 rounds of compression. The level to which sub-functions affect diffusion is subsequently measured, enabling potential prioritization of these sub-functions in future collision attacks. To accomplish this, the compression function is modified by removing sub-functions, and the diffusion of these new variants is measured. While the SAC measurements of each function eventually plateau close to the 50% target, no function, including the unmodified compression function, strictly meets the SAC, and multiple variant functions diffuse at comparatively slower rates.
Full article
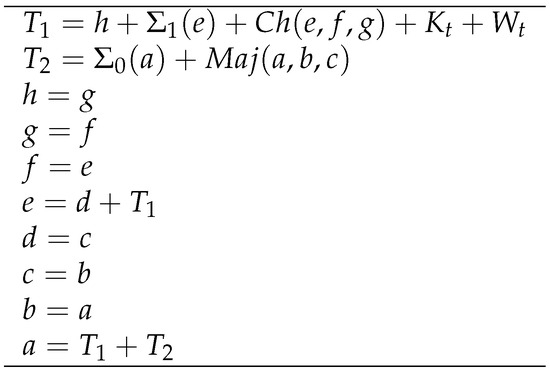
Figure 1
Figure 1
<p>One round of the SHA-256 compression function.</p> Full article ">Figure 2
<p>The minimum and maximum values from each row of the SAC dependency matrix of the full compression function with the message scheduler.</p> Full article ">Figure 3
<p>The minimum, maximum, and mean values from each round’s SAC dependency matrix with the message scheduler.</p> Full article ">Figure 4
<p>The minimum and maximum values from each row of the SAC dependency matrix of the full compression function without the message scheduler.</p> Full article ">Figure 5
<p>The minimum, maximum, and mean values from each round’s SAC dependency matrix without the message scheduler.</p> Full article ">Figure 6
<p>The minimum (Dashed), maximum (Dashed), and mean (Solid) values from each of the 64 SAC dependency matrices of compression function round variants with sub-functions-removed variants.</p> Full article ">
<p>One round of the SHA-256 compression function.</p> Full article ">Figure 2
<p>The minimum and maximum values from each row of the SAC dependency matrix of the full compression function with the message scheduler.</p> Full article ">Figure 3
<p>The minimum, maximum, and mean values from each round’s SAC dependency matrix with the message scheduler.</p> Full article ">Figure 4
<p>The minimum and maximum values from each row of the SAC dependency matrix of the full compression function without the message scheduler.</p> Full article ">Figure 5
<p>The minimum, maximum, and mean values from each round’s SAC dependency matrix without the message scheduler.</p> Full article ">Figure 6
<p>The minimum (Dashed), maximum (Dashed), and mean (Solid) values from each of the 64 SAC dependency matrices of compression function round variants with sub-functions-removed variants.</p> Full article ">
Open AccessArticle
A Novel Method of Secured Data Distribution Using Sharding Zkp and Zero Trust Architecture in Blockchain Multi Cloud Environment
by
Komala Rangappa, Arun Kumar Banavara Ramaswamy, Mahadeshwara Prasad and Shreyas Arun Kumar
Cryptography 2024, 8(3), 39; https://doi.org/10.3390/cryptography8030039 - 2 Sep 2024
Abstract
►▼
Show Figures
In the era of cloud computing, guaranteeing the safety and effectiveness of data management is of utmost importance. This investigation presents a novel approach that amalgamates the sharding concept, encryption, zero-knowledge proofs (zkp), and blockchain technology for secure data retrieval and data access
[...] Read more.
In the era of cloud computing, guaranteeing the safety and effectiveness of data management is of utmost importance. This investigation presents a novel approach that amalgamates the sharding concept, encryption, zero-knowledge proofs (zkp), and blockchain technology for secure data retrieval and data access control to improve data security, efficiency in cloud storage and migration. Further, we utilize user-specific digital wallets for secure encryption keys in order to encrypt the file before storing into the cloud. As Large files (greater than 50 MB) or Big data files (greater than 1 TB) require greater computational complexity, we leverage the sharding concept to enhance both space and time complexity in cloud storage. Hence, the large files are divided into shards and stored in different database servers. We also employ a blockchain smart contract to enhance secure retrieval of the file and also a secure access method, which ensures the privacy of the user. The zk-snark protocol is utilized to ensure the safe transfer of data between different cloud services. By utilizing this approach, data privacy is preserved, as only the proof of the data’s authenticity is shared with the verifier at the destination cloud, rather than the actual data themselves. The suggested method tackles important concerns related to data protection, privacy, and efficient resource utilization in cloud computing settings by ensuring it meets all the cloud policies required to store data. Since the environment maintains the privacy of the user data and the raw data of the user is not stored anywhere, the entire environment is set up as a Zero trust model.
Full article
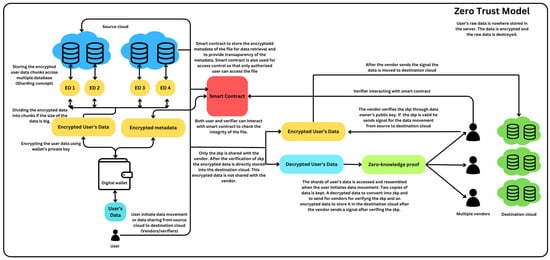
Figure 1
Figure 1
<p>Novel architecture of secure cloud environment.</p> Full article ">Figure 2
<p>Flow control diagram of sharding and encryption.</p> Full article ">Figure 3
<p>Flow control diagram of transmission of user data to destination cloud.</p> Full article ">Figure 4
<p>Analysis of time complexity for n no. of servers.</p> Full article ">Figure 5
<p>Gas consumption for each transaction type involved in the smart contract.</p> Full article ">Figure 6
<p>Zkp generation time and file migration time for different file sizes.</p> Full article ">Figure 7
<p>Comparison of our system with existing system.</p> Full article ">
<p>Novel architecture of secure cloud environment.</p> Full article ">Figure 2
<p>Flow control diagram of sharding and encryption.</p> Full article ">Figure 3
<p>Flow control diagram of transmission of user data to destination cloud.</p> Full article ">Figure 4
<p>Analysis of time complexity for n no. of servers.</p> Full article ">Figure 5
<p>Gas consumption for each transaction type involved in the smart contract.</p> Full article ">Figure 6
<p>Zkp generation time and file migration time for different file sizes.</p> Full article ">Figure 7
<p>Comparison of our system with existing system.</p> Full article ">
Open AccessArticle
Efficient Commutative PQC Algorithms on Isogenies of Edwards Curves
by
Anatoly Bessalov, Volodymyr Sokolov and Serhii Abramov
Cryptography 2024, 8(3), 38; https://doi.org/10.3390/cryptography8030038 - 27 Aug 2024
Abstract
The article presents the author’s works in the field of modifications and modeling of the Post-Quantum Cryptography (PQC) Commutative Supersingular Isogeny Diffie-Hellman (CSIDH) algorithm on non-cyclic supersingular Edwards curves and its predecessor Couveignes-Rostovtsev-Stolbunov (CRS) scheme on ordinary non-cyclic Edwards curves are reviewed. Lower
[...] Read more.
The article presents the author’s works in the field of modifications and modeling of the Post-Quantum Cryptography (PQC) Commutative Supersingular Isogeny Diffie-Hellman (CSIDH) algorithm on non-cyclic supersingular Edwards curves and its predecessor Couveignes-Rostovtsev-Stolbunov (CRS) scheme on ordinary non-cyclic Edwards curves are reviewed. Lower estimates of the computational speed gains of the modified algorithms over the original ones are obtained. The most significant results were obtained by choosing classes of non-cyclic Edwards curves connected as quadratic twist pairs instead of cyclic complete Edwards curves, as well as the method of algorithm randomization as an alternative to “constant time CSIDH”. It is shown that in the CSIDH and Commutative Supersingular Isogeny Key Encapsulation (CSIKE) algorithms, there are two independent cryptosystems with the possibility of parallel computation, eliminating the threat of side-channel attacks. There are four such cryptosystems for the CRS scheme. Integral lower bound estimates of the performance gain of the modified CSIDH algorithm are obtained at 1.5 × 29, and for the CRS scheme are 3 × 29.
Full article
(This article belongs to the Topic Trends and Prospects in Security, Encryption and Encoding)
Open AccessRetraction
RETRACTED: Liu et al. A Publicly Verifiable E-Voting System Based on Biometrics. Cryptography 2023, 7, 62
by
Jinhui Liu, Tianyi Han, Maolin Tan, Bo Tang, Wei Hu and Yong Yu
Cryptography 2024, 8(3), 37; https://doi.org/10.3390/cryptography8030037 - 23 Aug 2024
Abstract
The journal retracts the article, “A Publicly Verifiable E-Voting System Based on Biometrics” [...]
Full article
Open AccessArticle
Natural Language Processing for Hardware Security: Case of Hardware Trojan Detection in FPGAs
by
Jaya Dofe, Wafi Danesh, Vaishnavi More and Aaditya Chaudhari
Cryptography 2024, 8(3), 36; https://doi.org/10.3390/cryptography8030036 - 8 Aug 2024
Abstract
Field-programmable gate arrays (FPGAs) offer the inherent ability to reconfigure at runtime, making them ideal for applications such as data centers, cloud computing, and edge computing. This reconfiguration, often achieved through remote access, enables efficient resource utilization but also introduces critical security vulnerabilities.
[...] Read more.
Field-programmable gate arrays (FPGAs) offer the inherent ability to reconfigure at runtime, making them ideal for applications such as data centers, cloud computing, and edge computing. This reconfiguration, often achieved through remote access, enables efficient resource utilization but also introduces critical security vulnerabilities. An adversary could exploit this access to insert a dormant hardware trojan (HT) into the configuration bitstream, bypassing conventional security and verification measures. To address this security threat, we propose a supervised learning approach using deep recurrent neural networks (RNNs) for HT detection within FPGA configuration bitstreams. We explore two RNN architectures: basic RNN and long short-term memory (LSTM) networks. Our proposed method analyzes bitstream patterns, to identify anomalies indicative of malicious modifications. We evaluated the effectiveness on ISCAS 85 benchmark circuits of varying sizes and topologies, implemented on a Xilinx Artix-7 FPGA. The experimental results revealed that the basic RNN model showed lower accuracy in identifying HT-compromised bitstreams for most circuits. In contrast, the LSTM model achieved a significantly higher average accuracy of 93.5%. These results demonstrate that the LSTM model is more successful for HT detection in FPGA bitstreams. This research paves the way for using RNN architectures for HT detection in FPGAs, eliminating the need for time-consuming and resource-intensive reverse engineering or performance-degrading bitstream conversions.
Full article
(This article belongs to the Special Issue Emerging Topics in Hardware Security)
►▼
Show Figures
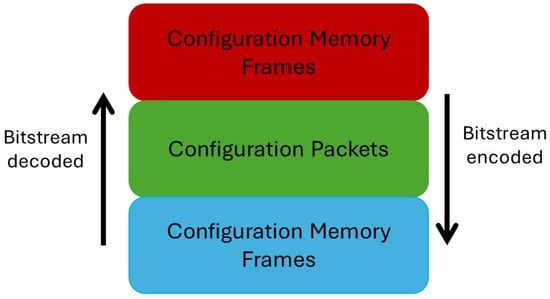
Figure 1
Figure 1
<p>Concept of a bitstream protocol stack for Xilinx 7 series FPGAs.</p> Full article ">Figure 2
<p>Xilinx configuration file formats. (Note: For (1), (2), (3) please refer to [<a href="#B22-cryptography-08-00036" class="html-bibr">22</a>]).</p> Full article ">Figure 3
<p>Steps in 7-series FPGA configuration.</p> Full article ">Figure 4
<p>Type 1 packet header format for Xilinx 7-series FPGA.</p> Full article ">Figure 5
<p>Opcode for Type 1 packet header.</p> Full article ">Figure 6
<p>Type 2 packet header format for Xilinx 7-series FPGA.</p> Full article ">Figure 7
<p>Frame address register description.</p> Full article ">Figure 8
<p>Conventional RNN architecture.</p> Full article ">Figure 9
<p>Hidden layer for conventional RNN.</p> Full article ">Figure 10
<p>Cell for LSTM architecture.</p> Full article ">Figure 11
<p>The .<span class="html-italic">bit</span> file format.</p> Full article ">Figure 12
<p>Data preprocessing algorithm.</p> Full article ">Figure 13
<p>Training RNN models on preprocessed bitstreams.</p> Full article ">Figure 14
<p>Training and validation accuracy over training epochs for RNN with step size 16.</p> Full article ">Figure 15
<p>Training and validation accuracy over training epochs for LSTM with step size 16.</p> Full article ">Figure 16
<p>Step size and accuracy trends for LSTM.</p> Full article ">Figure 17
<p>Example of latched RO.</p> Full article ">Figure 18
<p>Training and validation accuracy vs. step size for c17 benchmark.</p> Full article ">Figure 19
<p>Comparison of c17 performance metrics for step sizes 8 and 16.</p> Full article ">
<p>Concept of a bitstream protocol stack for Xilinx 7 series FPGAs.</p> Full article ">Figure 2
<p>Xilinx configuration file formats. (Note: For (1), (2), (3) please refer to [<a href="#B22-cryptography-08-00036" class="html-bibr">22</a>]).</p> Full article ">Figure 3
<p>Steps in 7-series FPGA configuration.</p> Full article ">Figure 4
<p>Type 1 packet header format for Xilinx 7-series FPGA.</p> Full article ">Figure 5
<p>Opcode for Type 1 packet header.</p> Full article ">Figure 6
<p>Type 2 packet header format for Xilinx 7-series FPGA.</p> Full article ">Figure 7
<p>Frame address register description.</p> Full article ">Figure 8
<p>Conventional RNN architecture.</p> Full article ">Figure 9
<p>Hidden layer for conventional RNN.</p> Full article ">Figure 10
<p>Cell for LSTM architecture.</p> Full article ">Figure 11
<p>The .<span class="html-italic">bit</span> file format.</p> Full article ">Figure 12
<p>Data preprocessing algorithm.</p> Full article ">Figure 13
<p>Training RNN models on preprocessed bitstreams.</p> Full article ">Figure 14
<p>Training and validation accuracy over training epochs for RNN with step size 16.</p> Full article ">Figure 15
<p>Training and validation accuracy over training epochs for LSTM with step size 16.</p> Full article ">Figure 16
<p>Step size and accuracy trends for LSTM.</p> Full article ">Figure 17
<p>Example of latched RO.</p> Full article ">Figure 18
<p>Training and validation accuracy vs. step size for c17 benchmark.</p> Full article ">Figure 19
<p>Comparison of c17 performance metrics for step sizes 8 and 16.</p> Full article ">
Open AccessArticle
A Note on the Quasigroup of Lai–Massey Structures
by
George Teşeleanu
Cryptography 2024, 8(3), 35; https://doi.org/10.3390/cryptography8030035 - 7 Aug 2024
Abstract
►▼
Show Figures
In our paper, we explore the consequences of replacing the commutative group operation used in Lai–Massey structures with a quasigroup operation. We introduce four quasigroup versions of the Lai–Massey structure and prove that for quasigroups isotopic with a group
In our paper, we explore the consequences of replacing the commutative group operation used in Lai–Massey structures with a quasigroup operation. We introduce four quasigroup versions of the Lai–Massey structure and prove that for quasigroups isotopic with a group
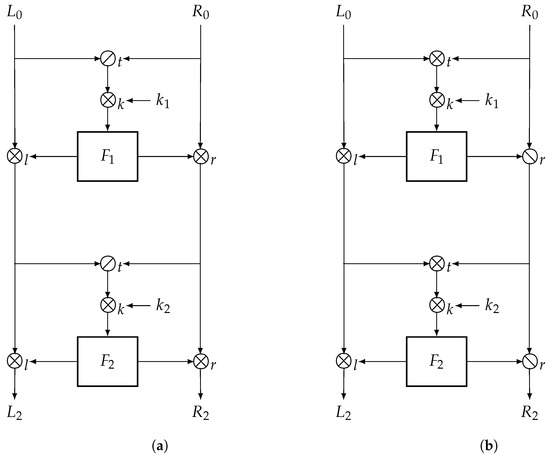
Figure 1
Figure 1
<p>Quasigroup Lai–Massey structures. (<b>a</b>) Symmetric version; (<b>b</b>) Asymmetric version.</p> Full article ">Figure 2
<p>Symmetric non-commutative group Lai–Massey structure (version 1).</p> Full article ">Figure 3
<p>Symmetric non-commutative group Lai–Massey structure (version 2).</p> Full article ">Figure 4
<p>Symmetric non-commutative group Lai–Massey structure (version 3).</p> Full article ">
<p>Quasigroup Lai–Massey structures. (<b>a</b>) Symmetric version; (<b>b</b>) Asymmetric version.</p> Full article ">Figure 2
<p>Symmetric non-commutative group Lai–Massey structure (version 1).</p> Full article ">Figure 3
<p>Symmetric non-commutative group Lai–Massey structure (version 2).</p> Full article ">Figure 4
<p>Symmetric non-commutative group Lai–Massey structure (version 3).</p> Full article ">
Open AccessArticle
A Novel Two-Level Protection Scheme against Hardware Trojans on a Reconfigurable CNN Accelerator
by
Zichu Liu, Jia Hou, Jianfei Wang and Chen Yang
Cryptography 2024, 8(3), 34; https://doi.org/10.3390/cryptography8030034 - 4 Aug 2024
Abstract
With the boom in artificial intelligence (AI), numerous reconfigurable convolution neural network (CNN) accelerators have emerged within both industry and academia, aiming to enhance AI computing capabilities. However, this rapid landscape has also witnessed a rise in hardware Trojan attacks targeted at CNN
[...] Read more.
With the boom in artificial intelligence (AI), numerous reconfigurable convolution neural network (CNN) accelerators have emerged within both industry and academia, aiming to enhance AI computing capabilities. However, this rapid landscape has also witnessed a rise in hardware Trojan attacks targeted at CNN accelerators, thereby posing substantial threats to the reliability and security of these reconfigurable systems. Despite this escalating concern, there exists a scarcity of security protection schemes explicitly tailored to counteract hardware Trojans embedded in reconfigurable CNN accelerators, and those that do exist exhibit notable deficiencies. Addressing these gaps, this paper introduces a dedicated security scheme designed to mitigate the vulnerabilities associated with hardware Trojans implanted in reconfigurable CNN accelerators. The proposed security protection scheme operates at two distinct levels: the first level is geared towards preventing the triggering of the hardware Trojan, while the second level focuses on detecting the presence of a hardware Trojan post-triggering and subsequently neutralizing its potential harm. Through experimental evaluation, our results demonstrate that this two-level protection scheme is capable of mitigating at least 99.88% of the harm cause by three different types of hardware Trojan (i.e., Trojan within RI, MAC and ReLU) within reconfigurable CNN accelerators. Furthermore, this scheme can prevent hardware Trojans from triggering whose trigger signal is derived from a processing element (PE). Notably, the proposed scheme is implemented and validated on a Xilinx Zynq XC7Z100 platform.
Full article
(This article belongs to the Special Issue Emerging Topics in Hardware Security)
►▼
Show Figures
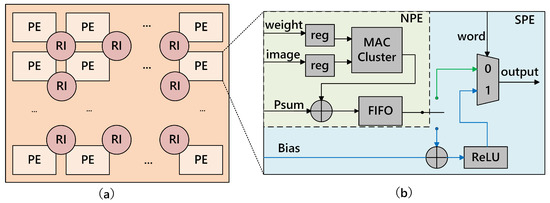
Figure 1
Figure 1
<p>The structure of RPA. (<b>a</b>) Overview of RPA; (<b>b</b>) the structure of PE.</p> Full article ">Figure 2
<p>Hardware Trojan in RI.</p> Full article ">Figure 3
<p>Hardware Trojan of (<b>a</b>) MAC and (<b>b</b>) ReLU.</p> Full article ">Figure 4
<p>Overview of the targeting hardware Trojan.</p> Full article ">Figure 5
<p>The proposed protection scheme. (<b>a</b>) Overview of the scheme; (<b>b</b>) detail of the scheme.</p> Full article ">Figure 6
<p>The “PE Space Randomization” scheme.</p> Full article ">Figure 7
<p>Overview of Voting.</p> Full article ">Figure 8
<p>IORD for MAC.</p> Full article ">Figure 9
<p>IORD for ReLU.</p> Full article ">Figure 10
<p>The PE collaboration correction solution.</p> Full article ">Figure 11
<p>Protection effectiveness of Voting.</p> Full article ">Figure 12
<p>Protection effectiveness of the PCC.</p> Full article ">Figure 13
<p>Protection effectiveness of two-level prevention scheme.</p> Full article ">
<p>The structure of RPA. (<b>a</b>) Overview of RPA; (<b>b</b>) the structure of PE.</p> Full article ">Figure 2
<p>Hardware Trojan in RI.</p> Full article ">Figure 3
<p>Hardware Trojan of (<b>a</b>) MAC and (<b>b</b>) ReLU.</p> Full article ">Figure 4
<p>Overview of the targeting hardware Trojan.</p> Full article ">Figure 5
<p>The proposed protection scheme. (<b>a</b>) Overview of the scheme; (<b>b</b>) detail of the scheme.</p> Full article ">Figure 6
<p>The “PE Space Randomization” scheme.</p> Full article ">Figure 7
<p>Overview of Voting.</p> Full article ">Figure 8
<p>IORD for MAC.</p> Full article ">Figure 9
<p>IORD for ReLU.</p> Full article ">Figure 10
<p>The PE collaboration correction solution.</p> Full article ">Figure 11
<p>Protection effectiveness of Voting.</p> Full article ">Figure 12
<p>Protection effectiveness of the PCC.</p> Full article ">Figure 13
<p>Protection effectiveness of two-level prevention scheme.</p> Full article ">
Highly Accessed Articles
Latest Books
E-Mail Alert
News
Topics
Topic in
Applied Sciences, Cryptography, JCP, JSAN, Sci, Symmetry
Trends and Prospects in Security, Encryption and Encoding
Topic Editors: Ki-Hyun Jung, Luis Javier García VillalbaDeadline: 31 December 2024
Topic in
Electronics, JCP, Mathematics, Sustainability, Remote Sensing, IJGI, Cryptography, Blockchains
Recent Advances in Security, Privacy, and Trust
Topic Editors: Jun Feng, Changqing Luo, Mamoun AlazabDeadline: 31 December 2025
Conferences
Special Issues
Special Issue in
Cryptography
Role of Cryptography in Network Security
Guest Editors: Krzysztof Szczypiorski, Borislav StoyanovDeadline: 30 November 2024
Special Issue in
Cryptography
Emerging Topics in Hardware Security
Guest Editor: Jim PlusquellicDeadline: 10 December 2024
Special Issue in
Cryptography
Privacy-Preserving Blockchain-Based Authentication Scheme
Guest Editor: Lu YuDeadline: 30 December 2024
Special Issue in
Cryptography
Advances in Authentication, Authorization and Privacy for Securing Smart Communications
Guest Editors: Cheng-Chi Lee, Tuan-Vinh Le, Chun-Ta Li, Dinh-Thuan Do, Agbotiname Lucky ImoizeDeadline: 31 December 2024
